Hands-on lab exercises implementation of DoS and MiM attacks using ARP cache poisoning | Semantic Scholar

PDF) Hands-on lab exercises implementation of DoS and MiM attacks using ARP cache poisoning | Zouheir Trabelsi - Academia.edu

TP LINK 22*10G/10gb SFP+ ports Ethernet switch 10Gbps interface board 10 Gigabit switch 10000Mbps TL ST8022F LPU DHCP ARP DoS|Network Switches| - AliExpress

Jean Arp, Overturned Blue Shoe with Two Heels under a Black Vault on ArtStack #jean-arp #art | Jean arp, Peggy guggenheim, Con dos tacones

Hands-on lab exercises implementation of DoS and MiM attacks using ARP cache poisoning | Semantic Scholar
GitHub - DavidBrosnan/asymptote-arp-dos: Python module of discovering hosts on Local Area Network, and ARP poisoning for a Denial of Service attack on a number of hosts
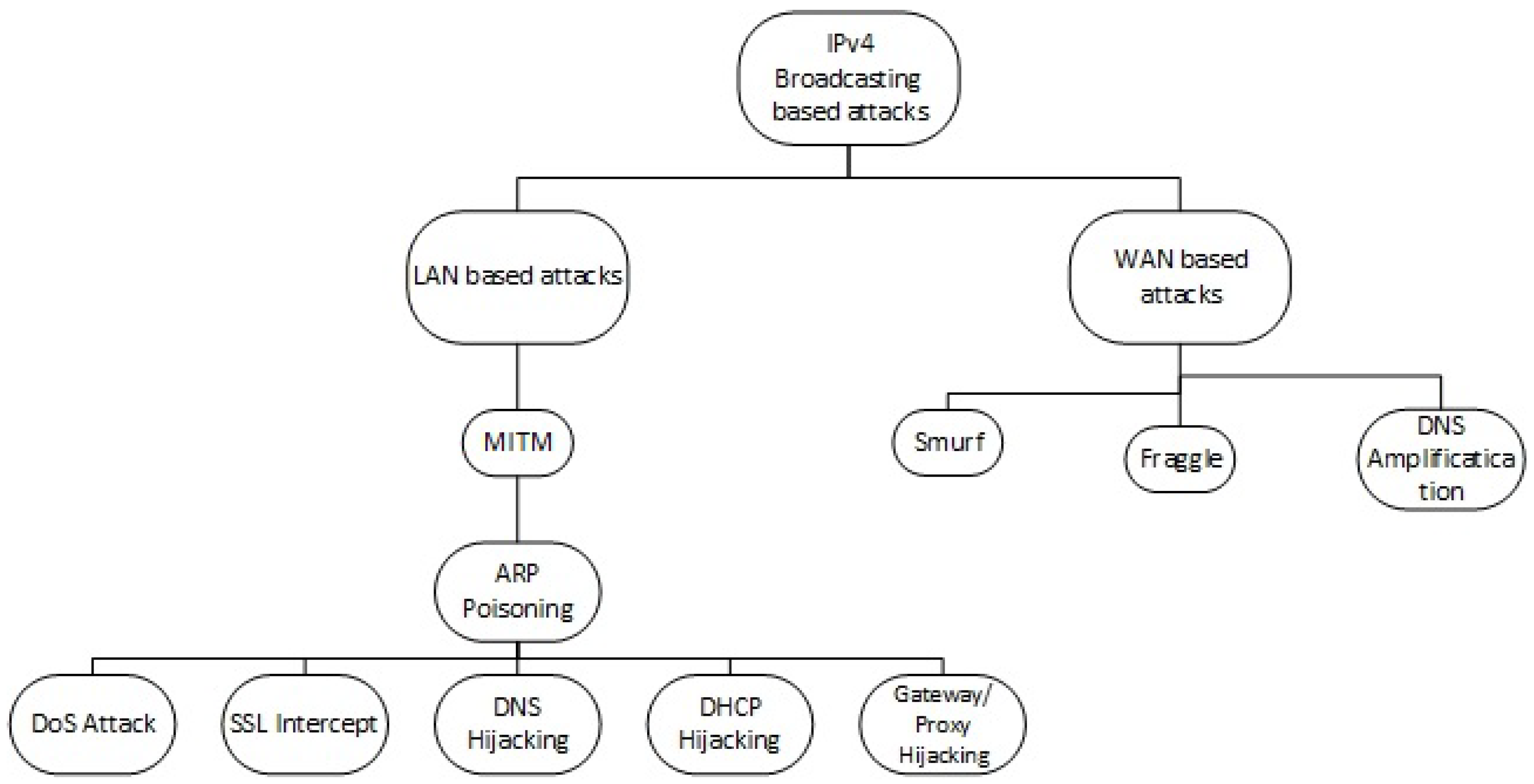
Electronics | Free Full-Text | PrECast: An Efficient Crypto-Free Solution for Broadcast-Based Attacks in IPv4 Networks | HTML
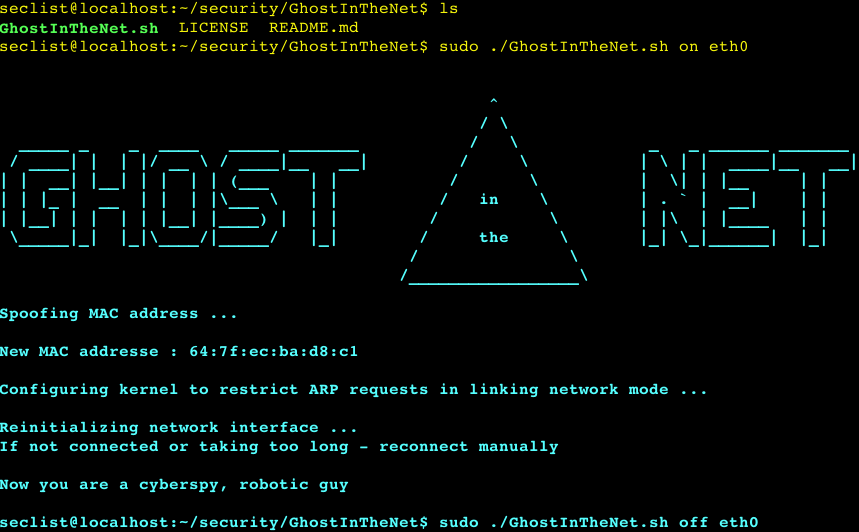

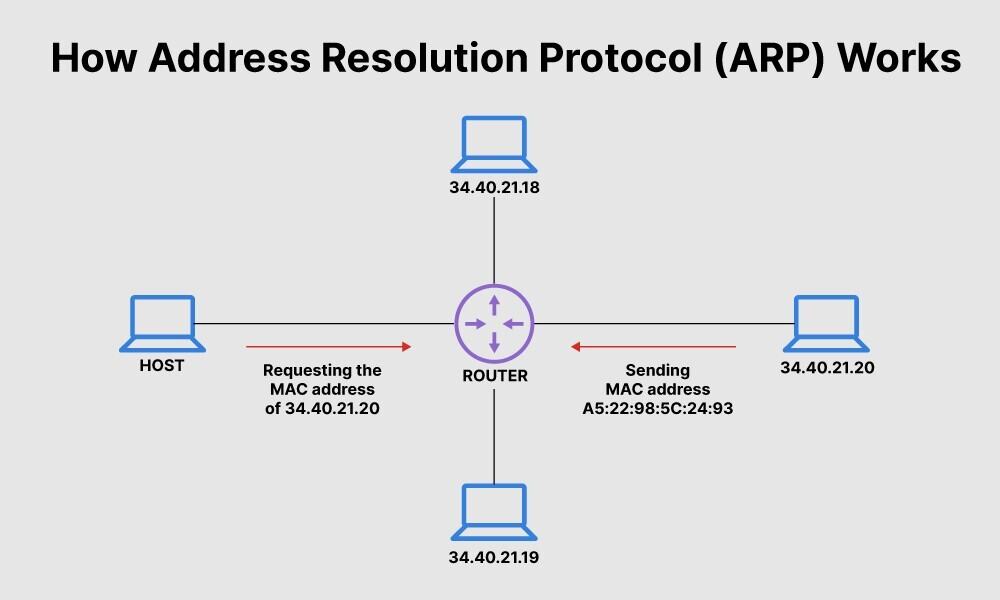
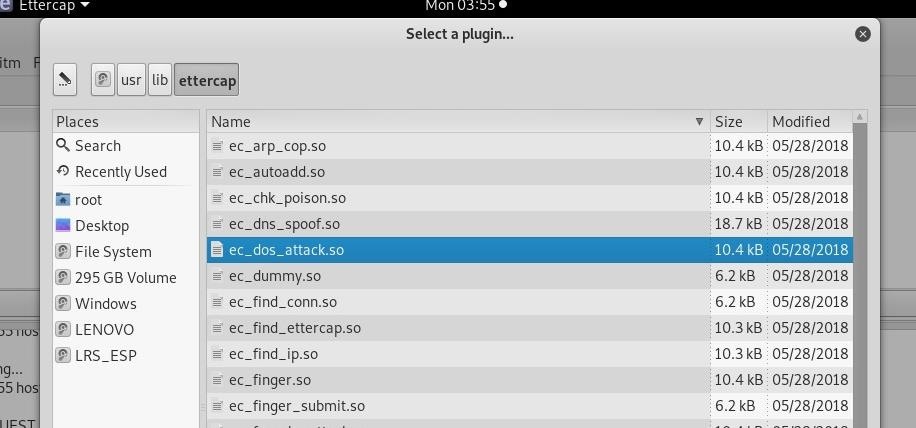

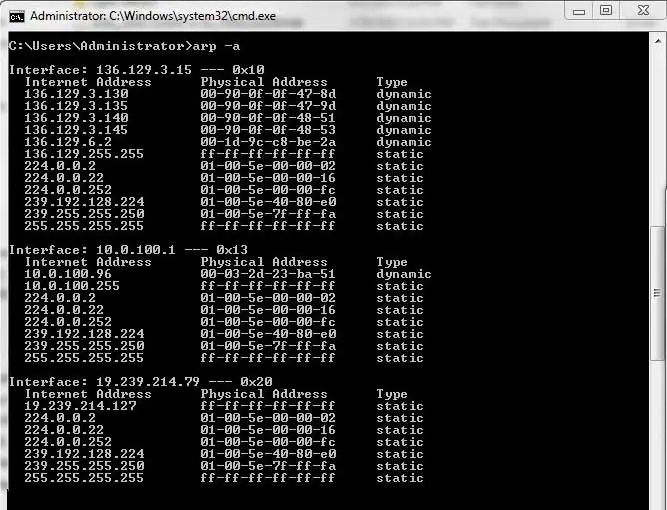


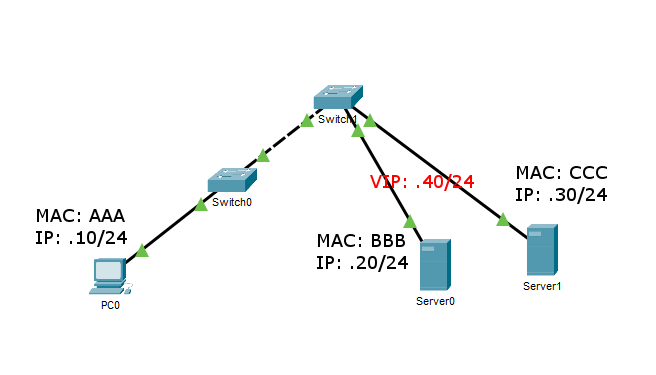

![Tutorial on ARP - Command-Line Tool to View and Manage your ARP Cache [Examples] Tutorial on ARP - Command-Line Tool to View and Manage your ARP Cache [Examples]](https://www.meridianoutpost.com/resources/articles/command-line/images/arp-s.png)