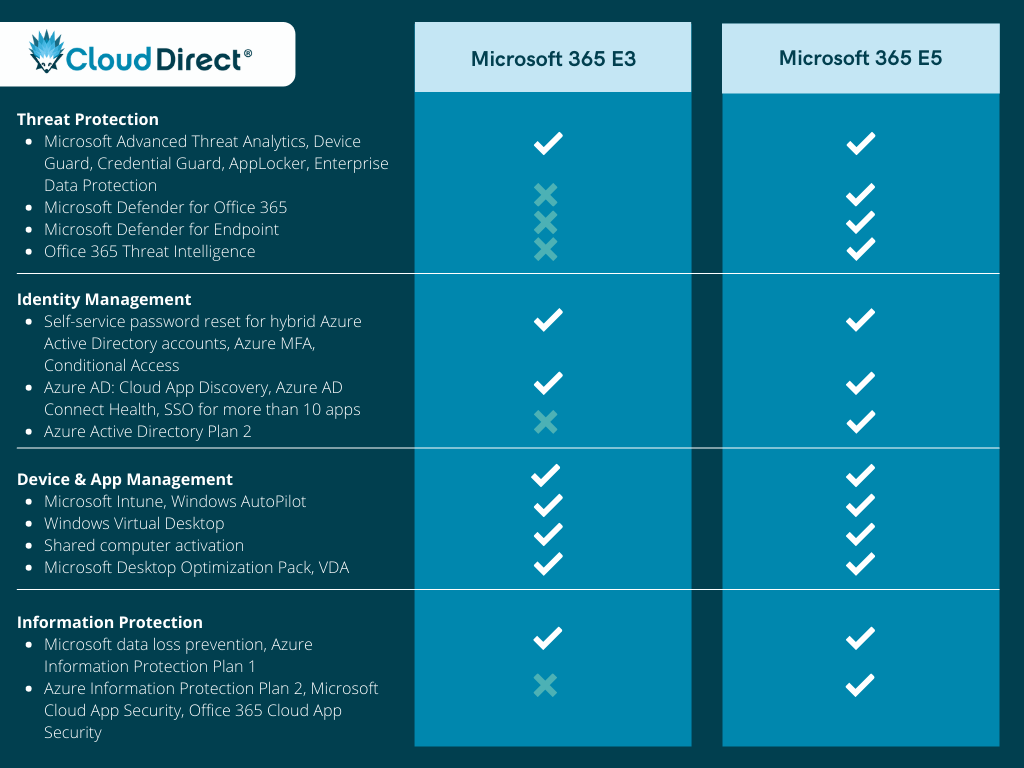
4 Most Important Security Features Your Web Hosting Provider Must Have to Prevent Cyber Attack | CyberCureME
Cyber Security Module Features For Organization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Features of Microsoft's Cloud Computing Technology - Multisoft Virtual Academy - Blog | Cloud computing technology, Cloud computing, Cyber security awareness