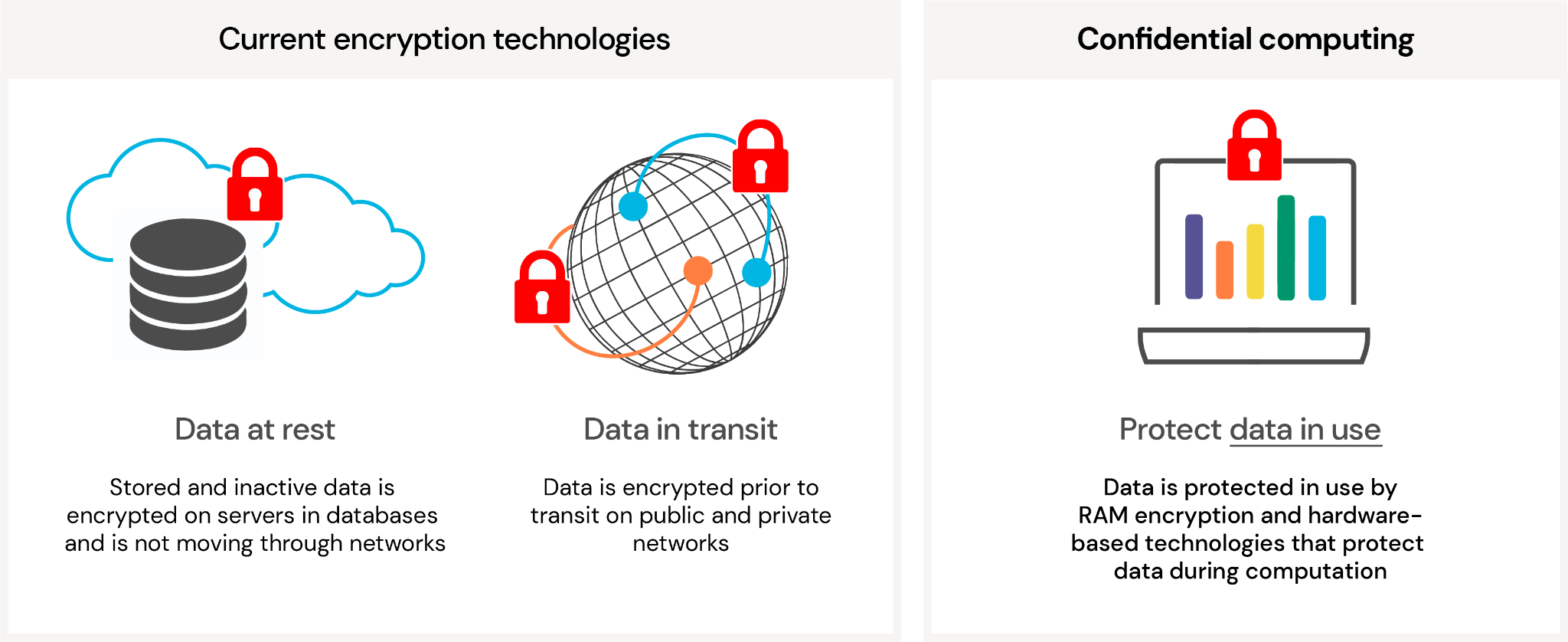
Confidential Computing and Machine Learning — Running TensorFlow Models Inside Secure Enclaves with Fortanix Runtime Encryption® | by Fortanix | Medium
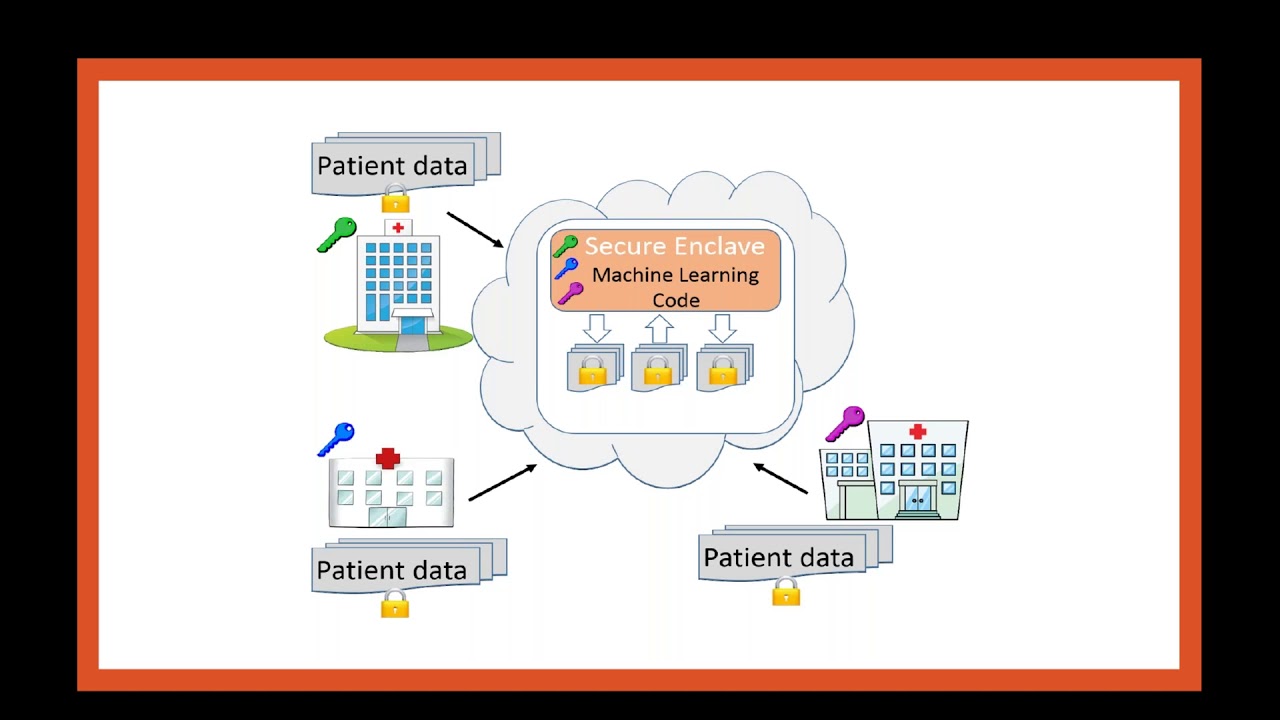
Secure Multiparty Machine Learning with Azure Confidential Computing - European SharePoint, Office 365 & Azure Conference, 2022

Brendan Burns: Everything You Need to Know About Confidential Computing and Containers – The New Stack