Hacked computer icon isometric vector. Skull, bone on computer screen, css file. Hacking attack, internet security, data protection Stock Vector Image & Art - Alamy

Software source code. Hacker breaching net security. Computer program preview. CSS, JavaScript and HTML usage. Displaying program code on computer. Mobile app developer. Stock Photo | Adobe Stock

What's the Latest in Cybersecurity? Key Takeaways from The University of Miami's First Annual Cybersecurity Conference | News | CAPSICUM | Digital Forensics, Investigations, Cyber Security

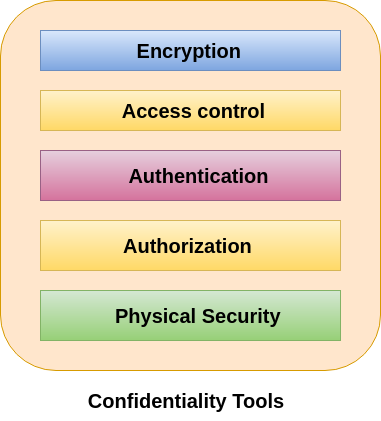
Css security in Networks-css-ps2 1 Computer Systems Security Security in Networks (Security Controls) Topic 2 Pirooz Saeidi Source: Pfleeger, Chapter ppt download
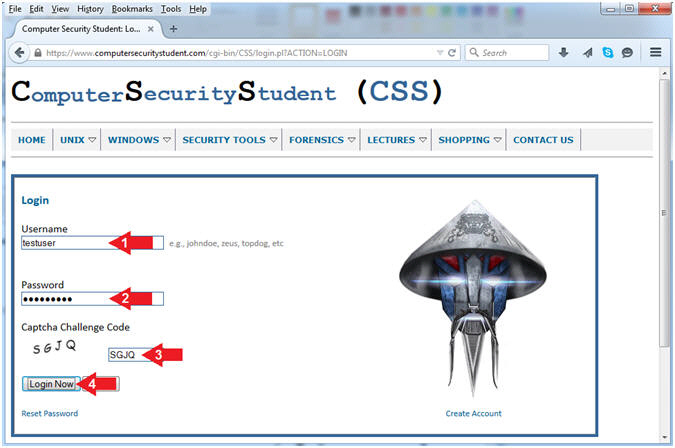
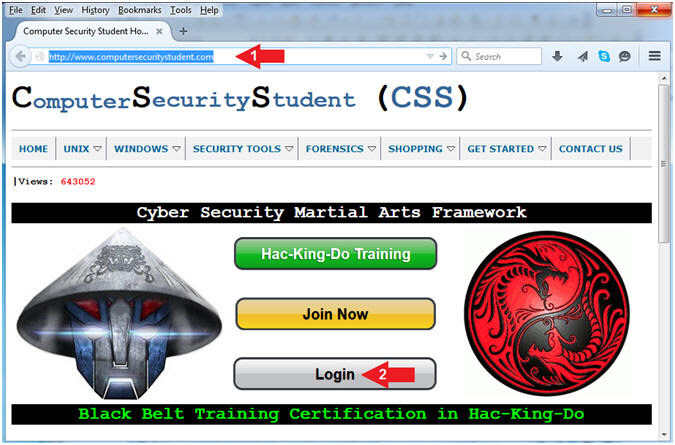
PDF) Computer Systems Security - CSS- ReShare System - File Sharing System Through a Web Application Portal