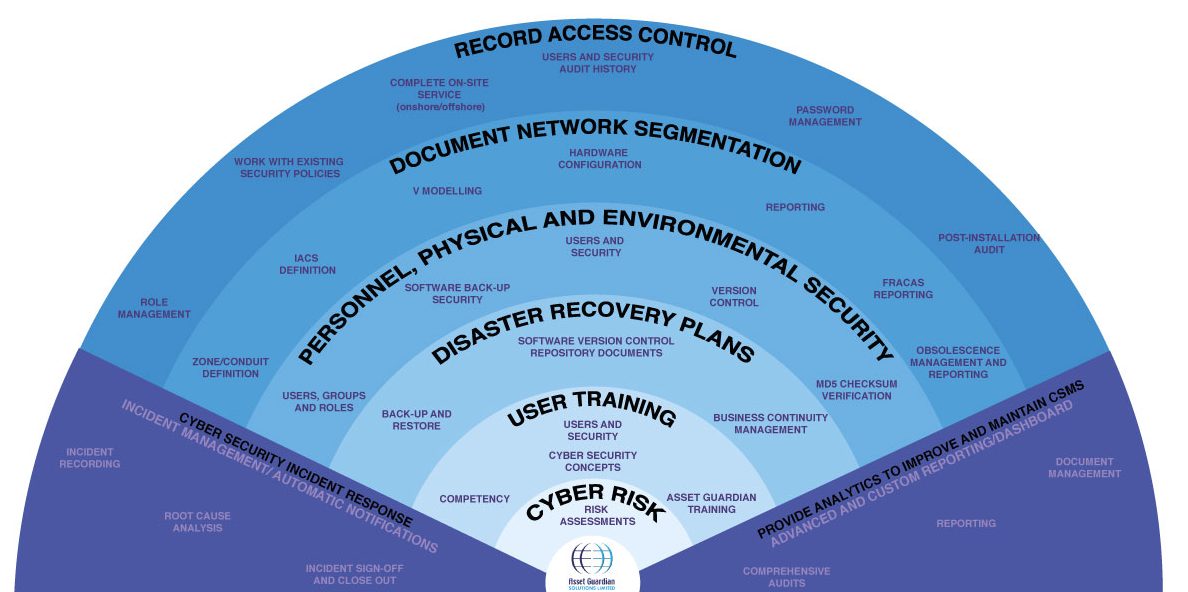
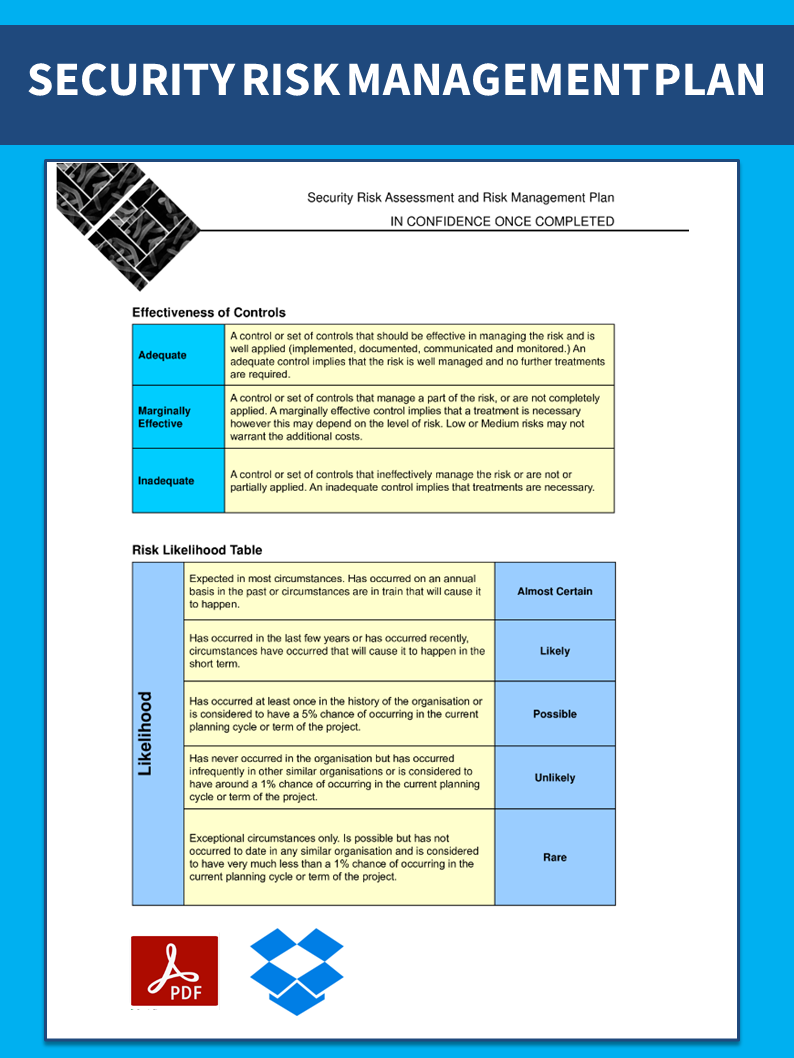
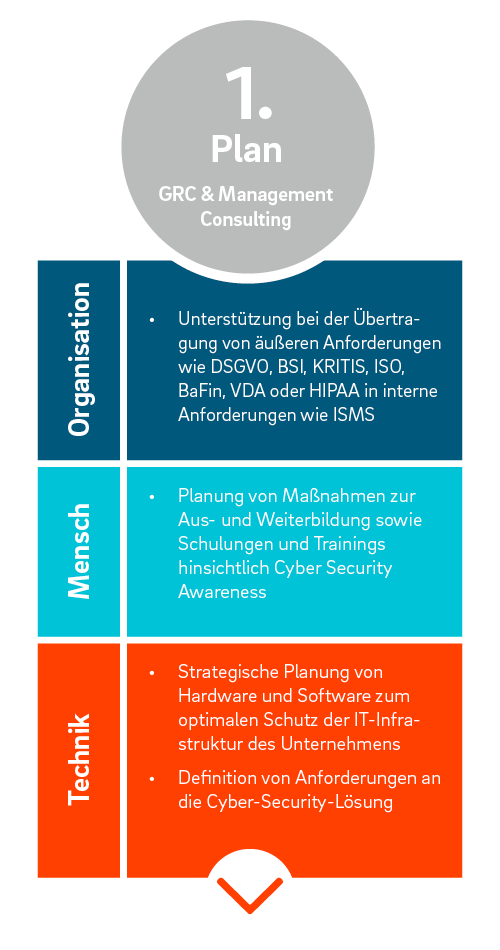
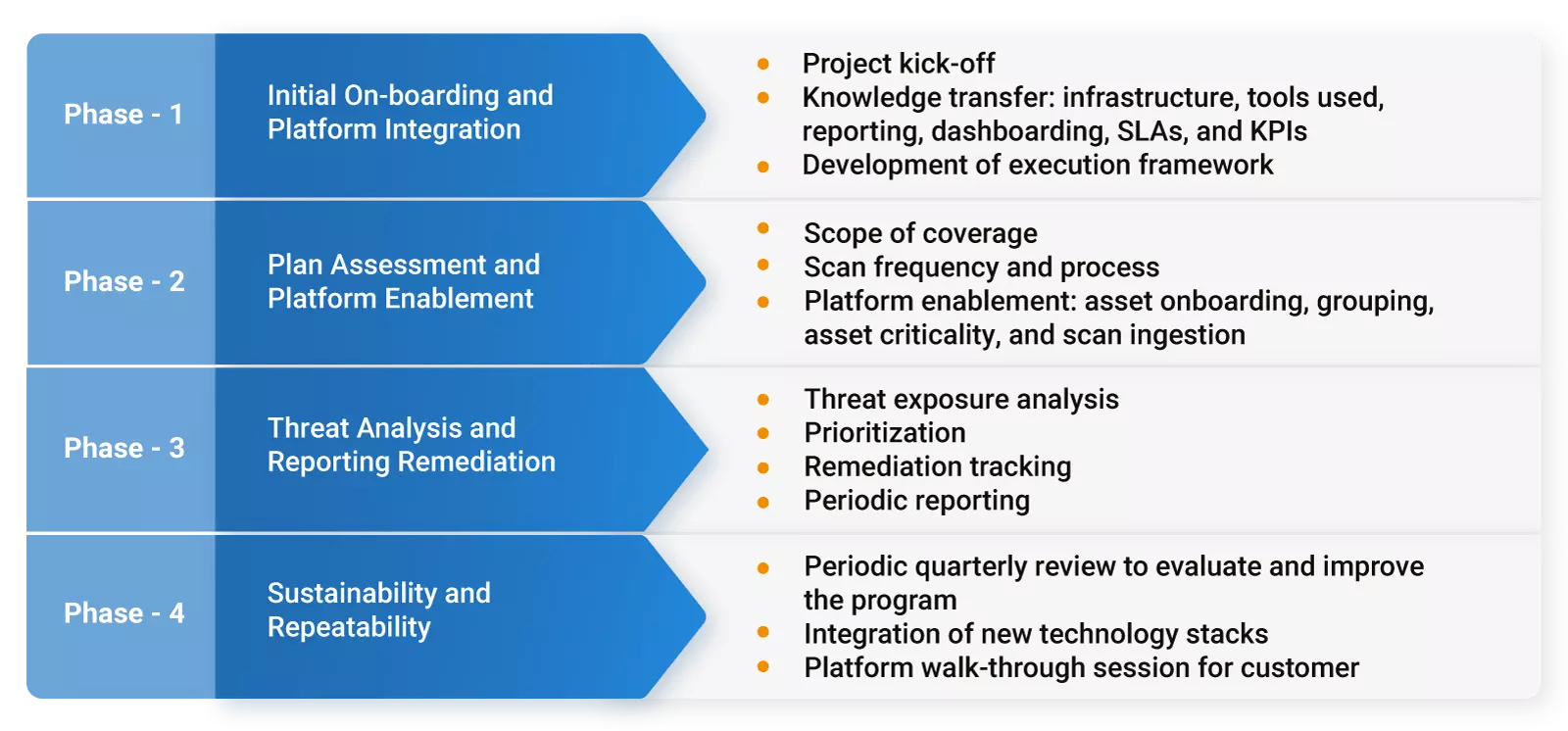
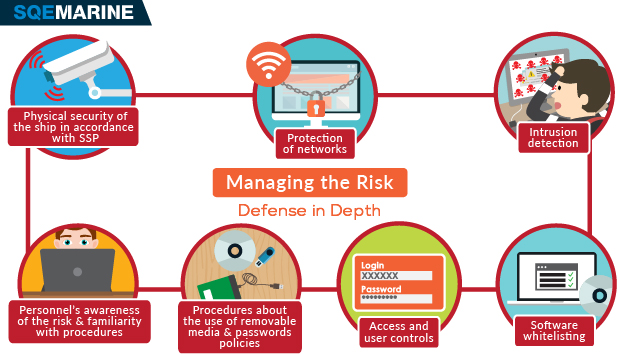
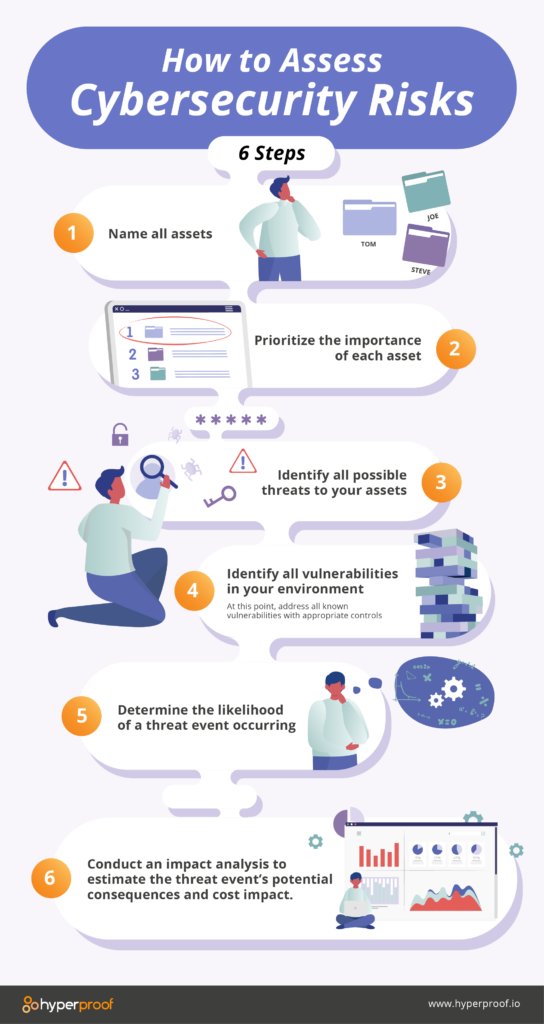
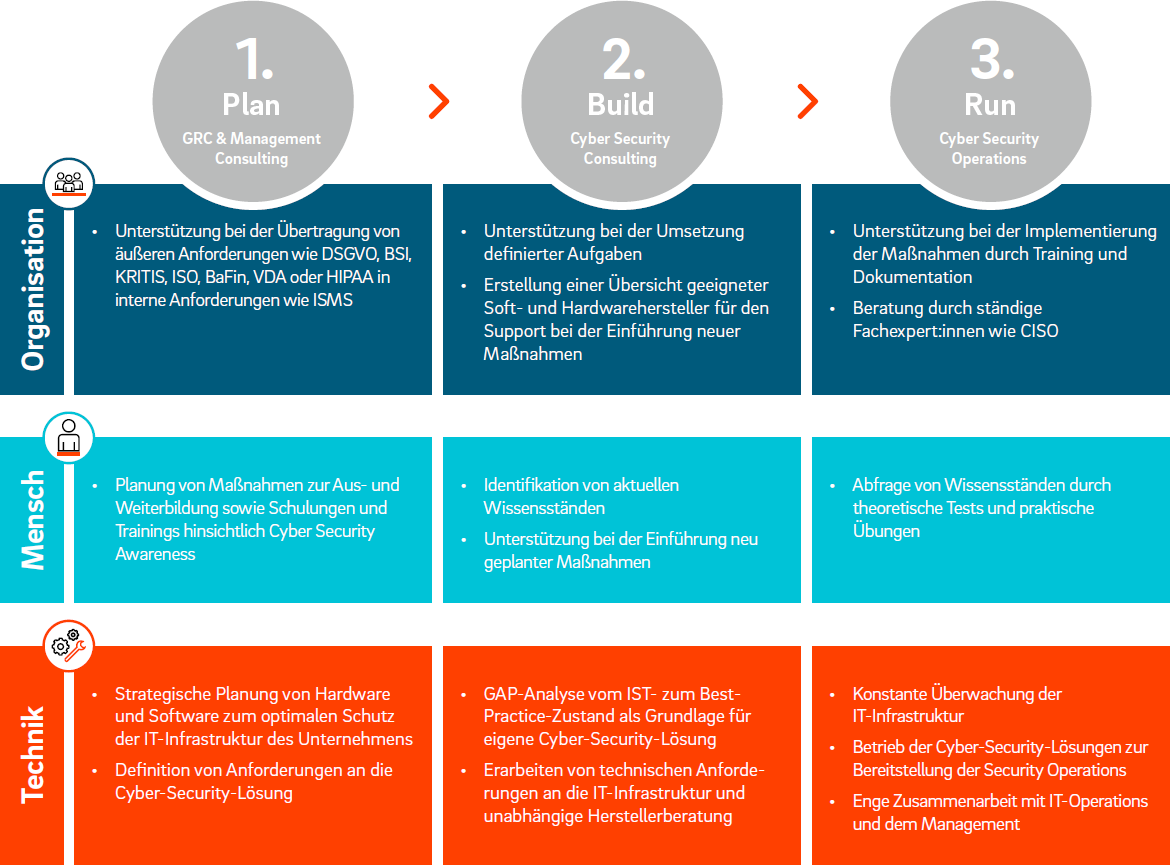
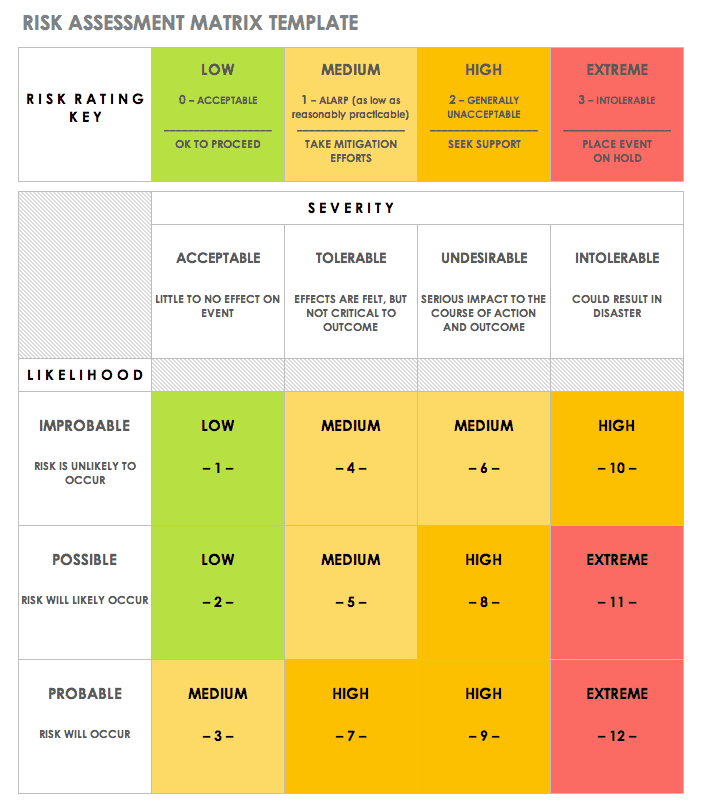
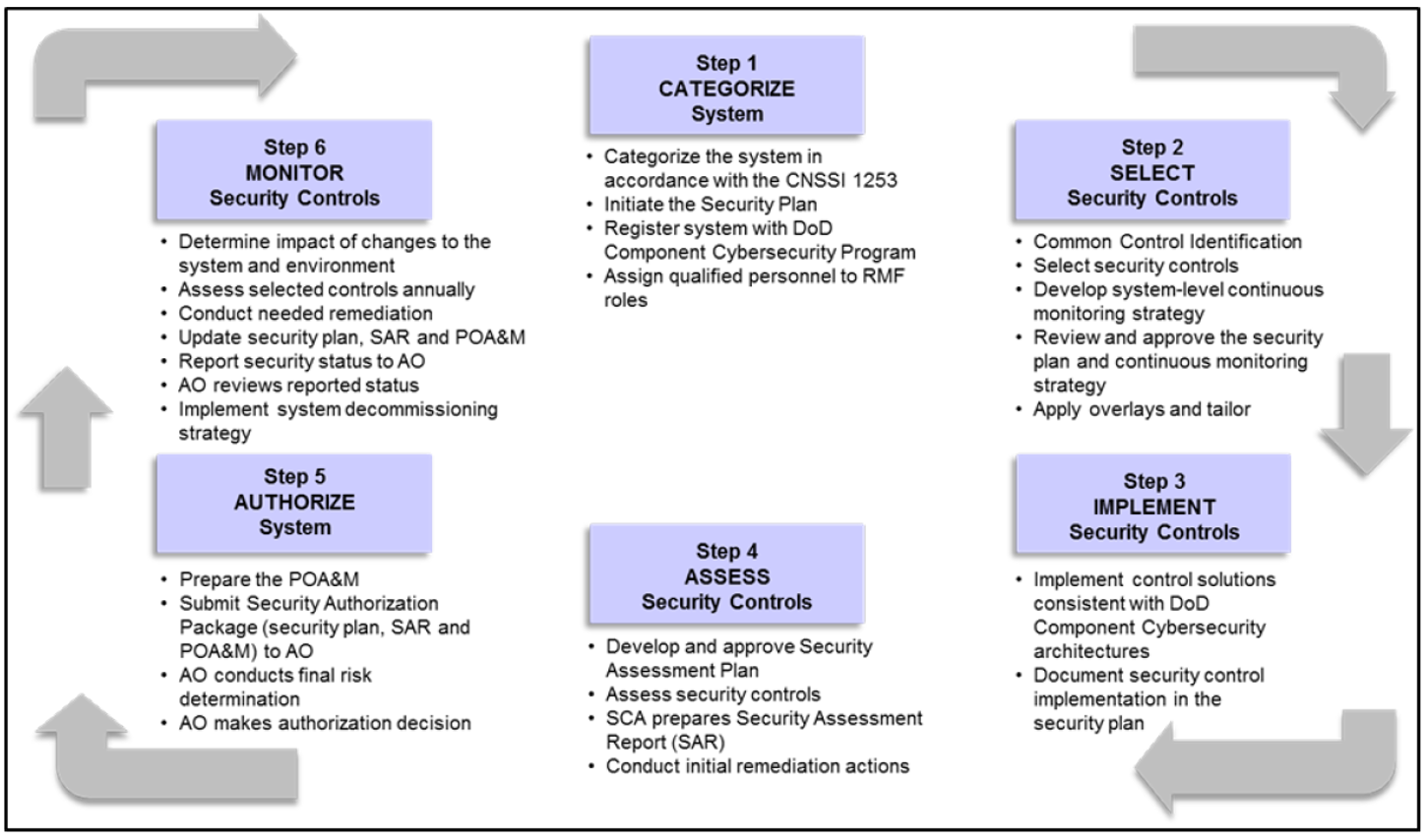
Cyber Security Risk Management Plan Multitiered Risk Management Framework Diagram Inspiration PDF - PowerPoint Templates
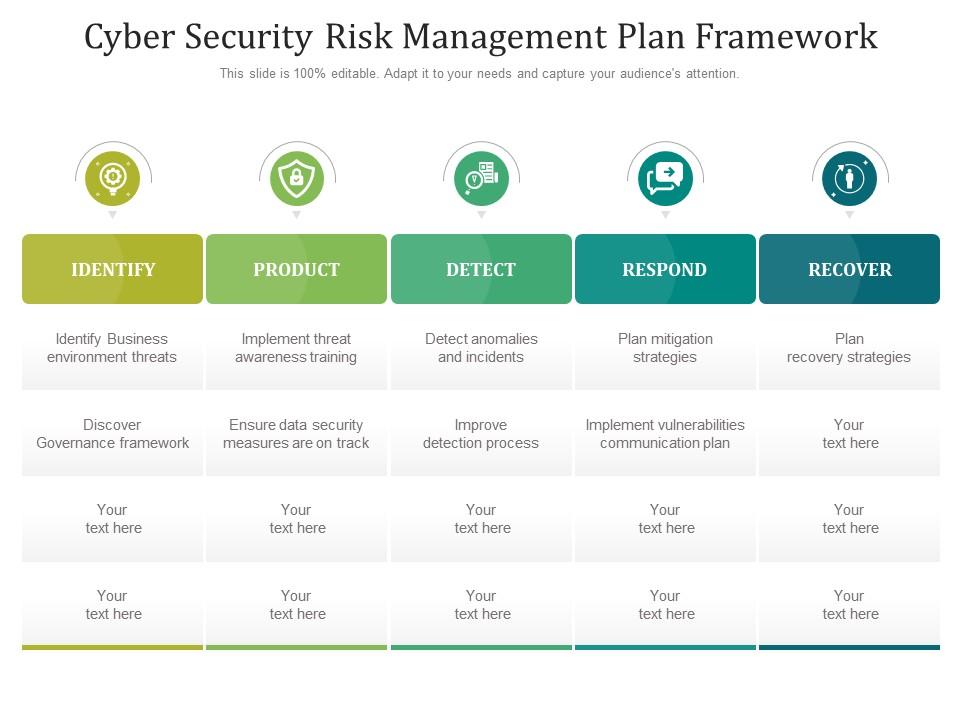
Cyber Security Risk Management Plan Framework | Presentation Graphics | Presentation PowerPoint Example | Slide Templates