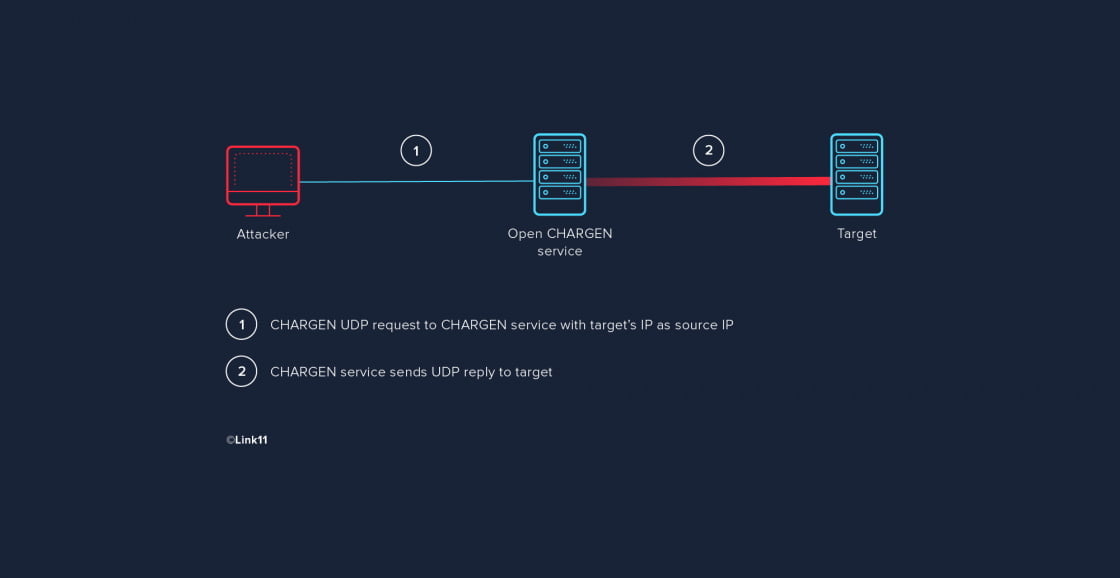
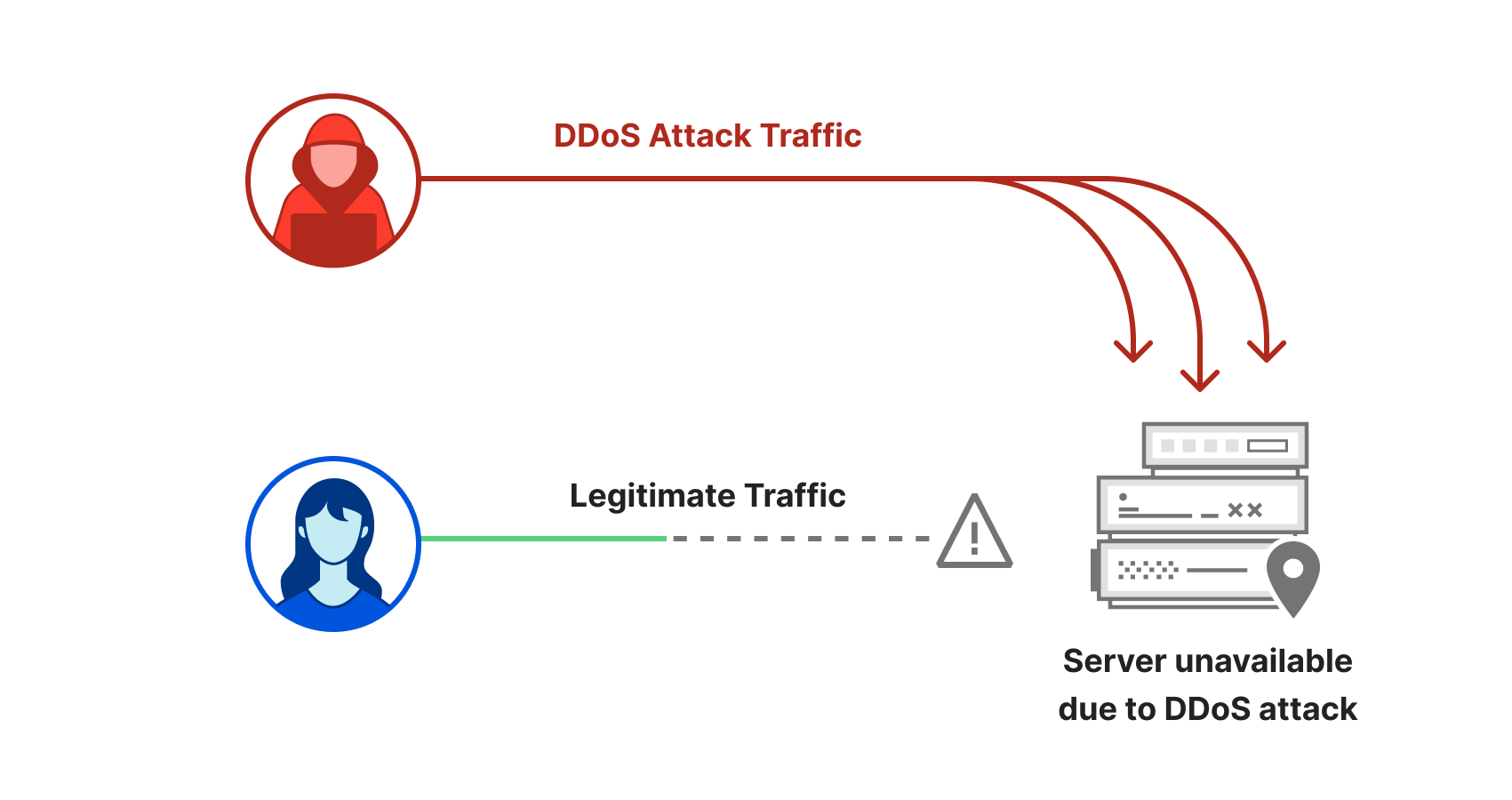
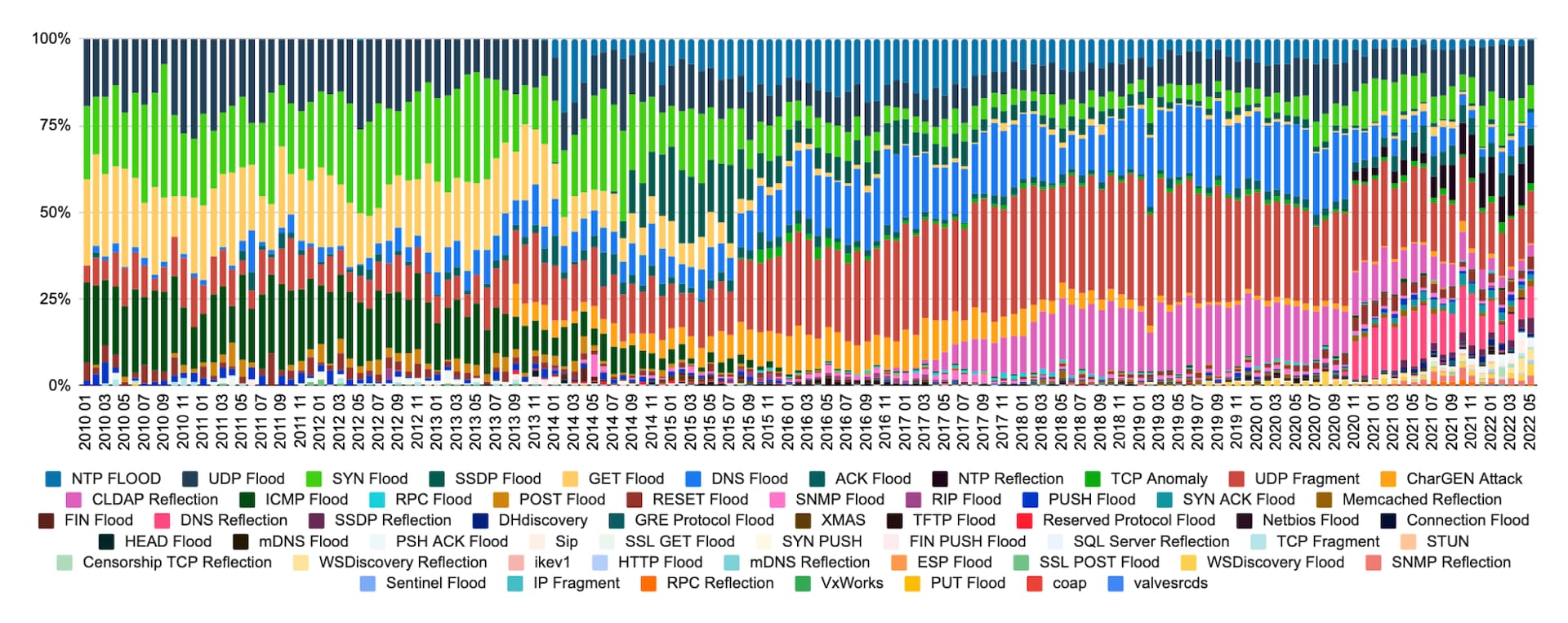
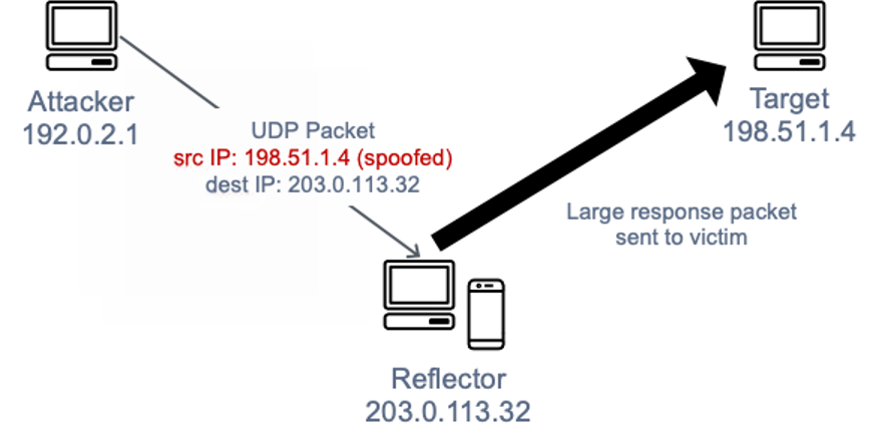
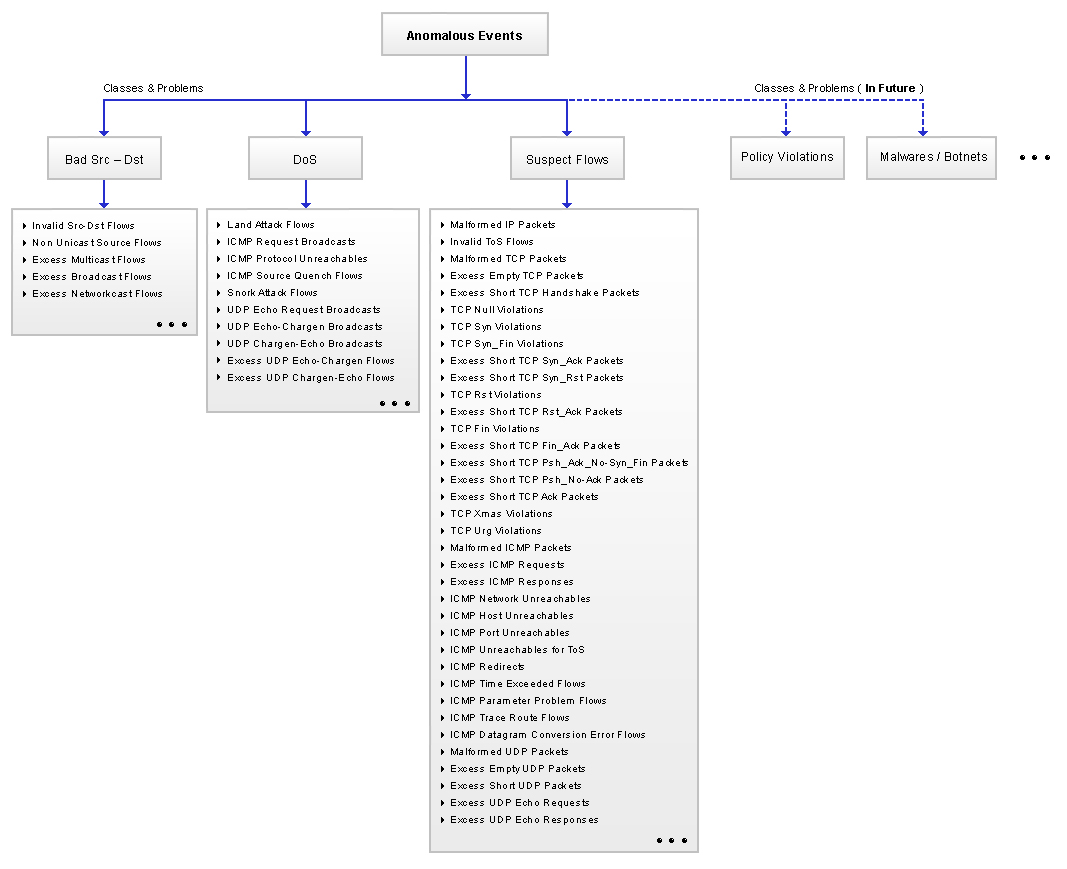
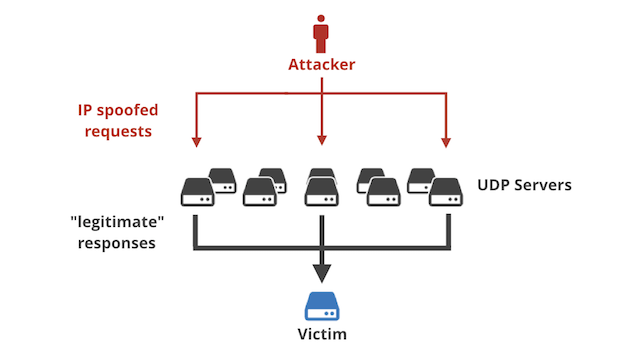
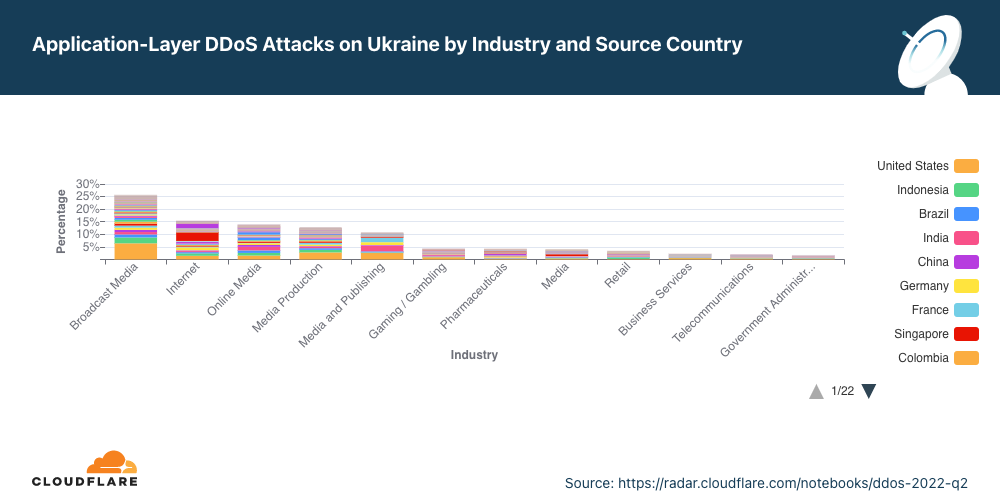
The distribution of DoS and DDoS attack inside the CICDDoS2019 dataset... | Download Scientific Diagram
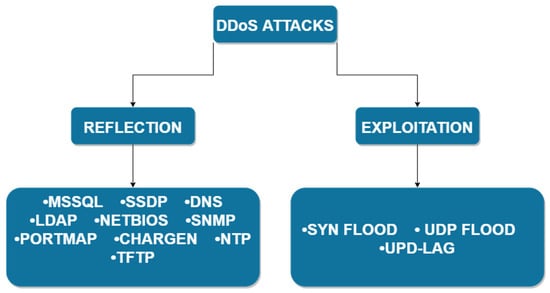
Applied Sciences | Free Full-Text | Multi-Classifier of DDoS Attacks in Computer Networks Built on Neural Networks

A survey and taxonomy of DoS attacks in cloud computing - Masdari - 2016 - Security and Communication Networks - Wiley Online Library
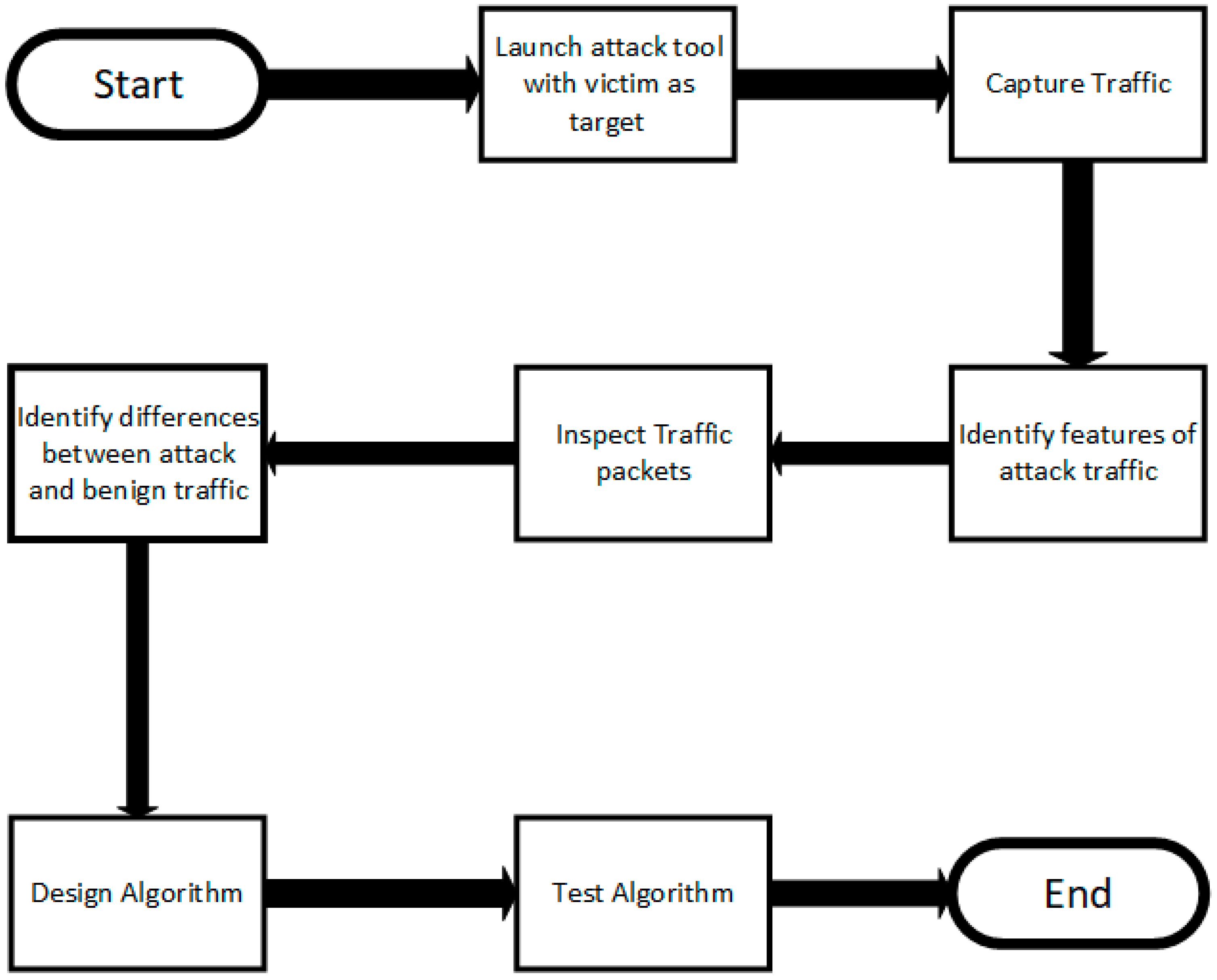
Computers | Free Full-Text | A Proposed DoS Detection Scheme for Mitigating DoS Attack Using Data Mining Techniques