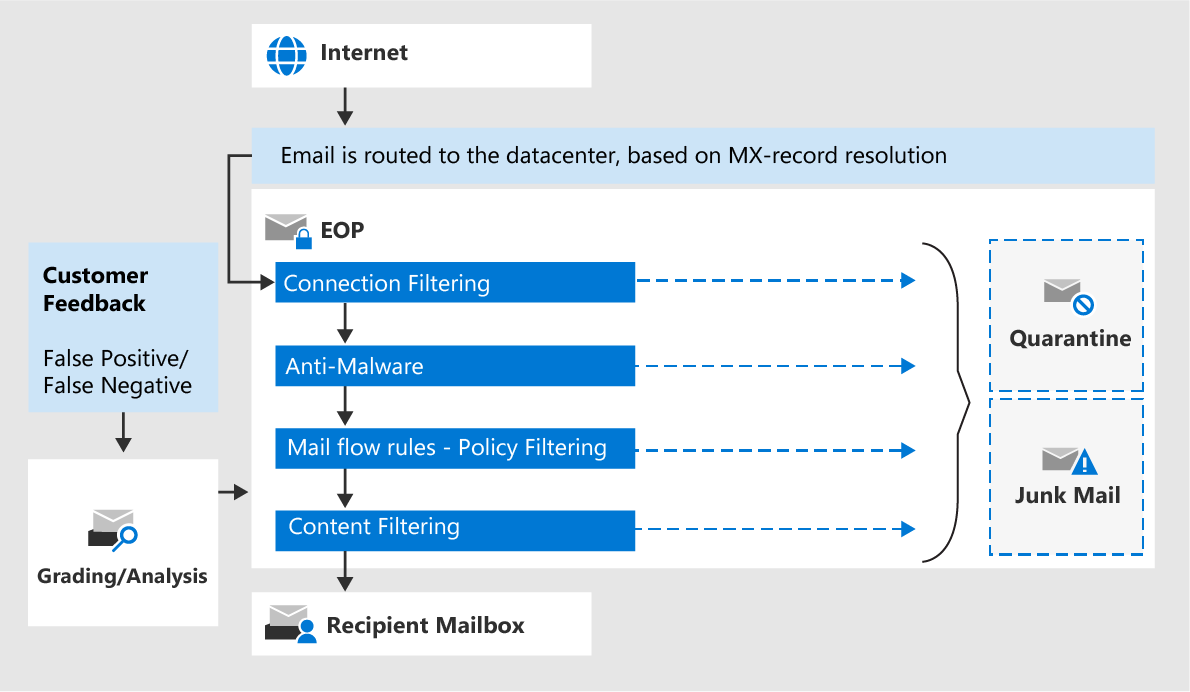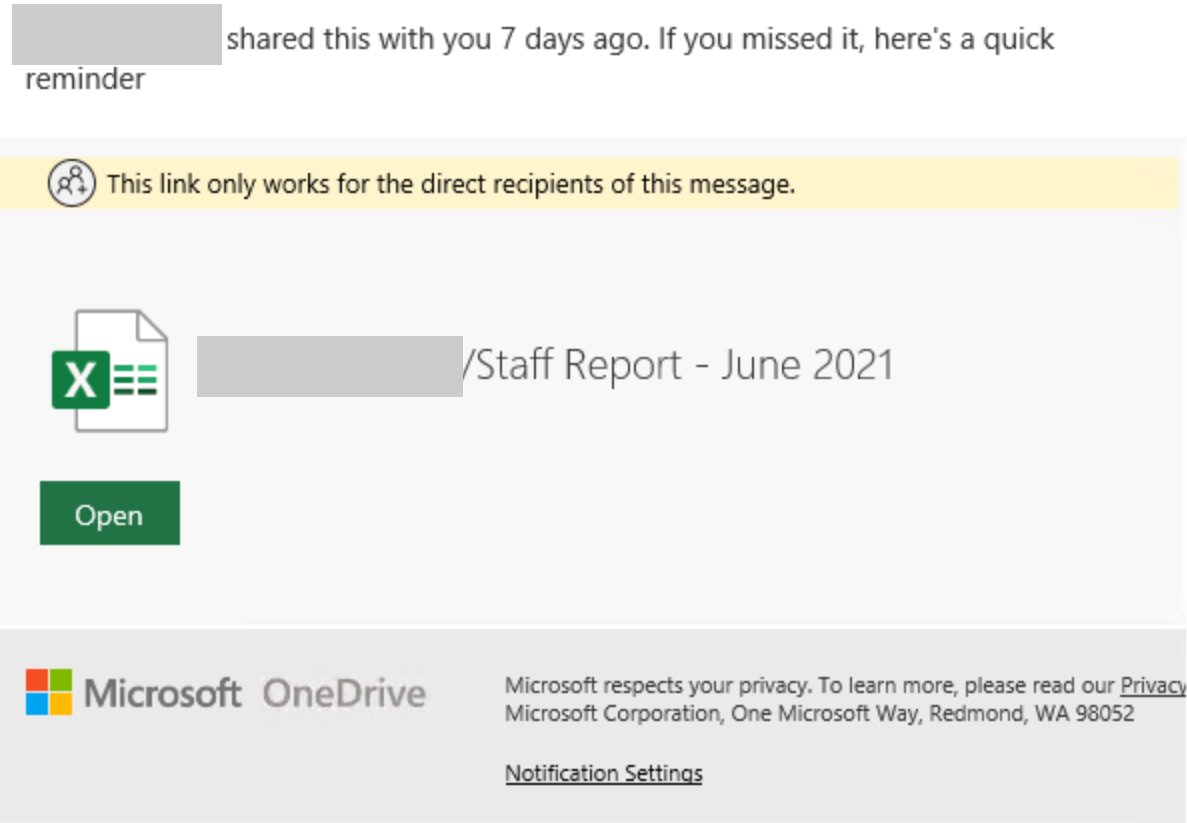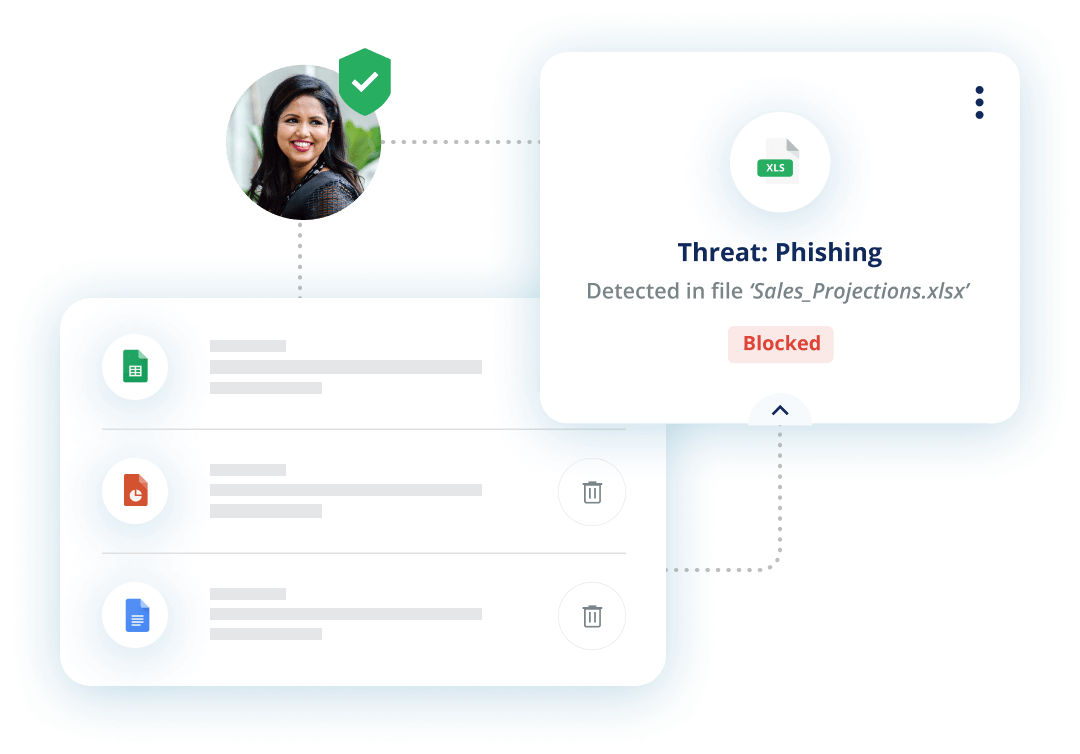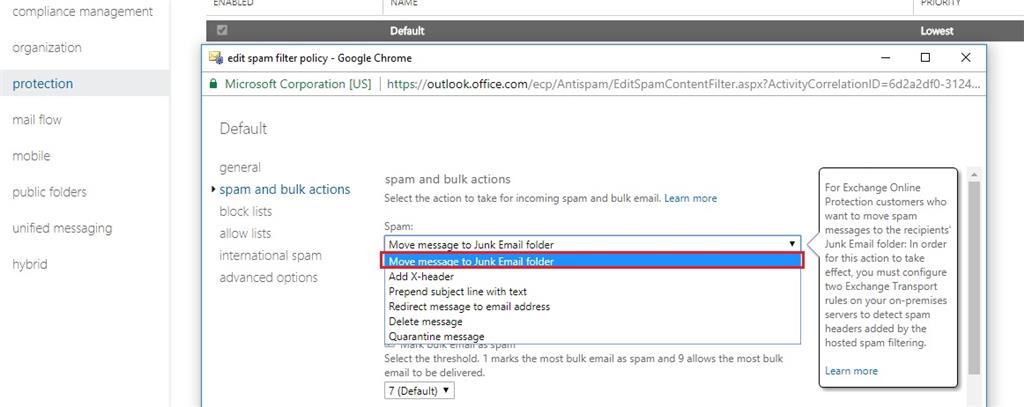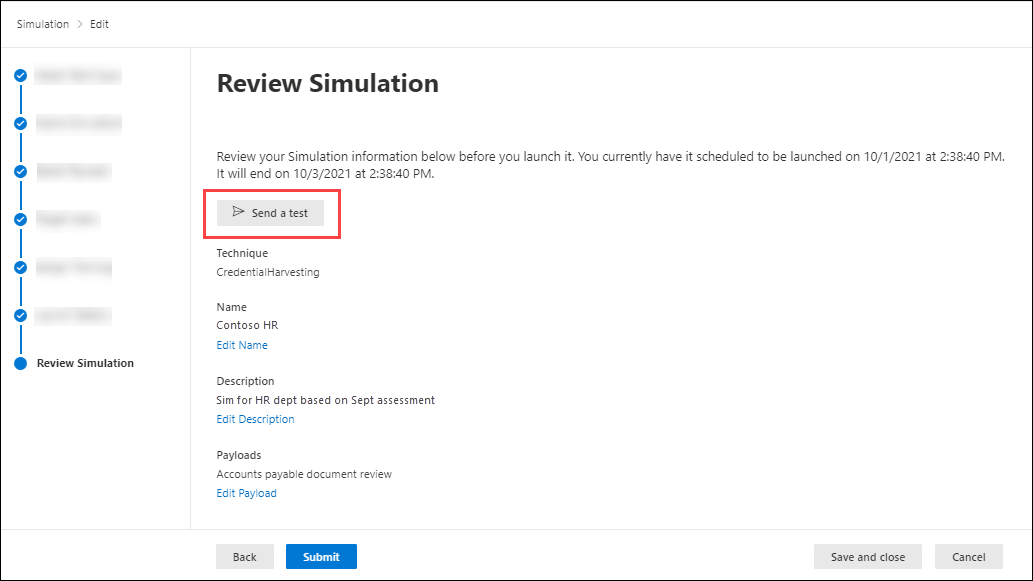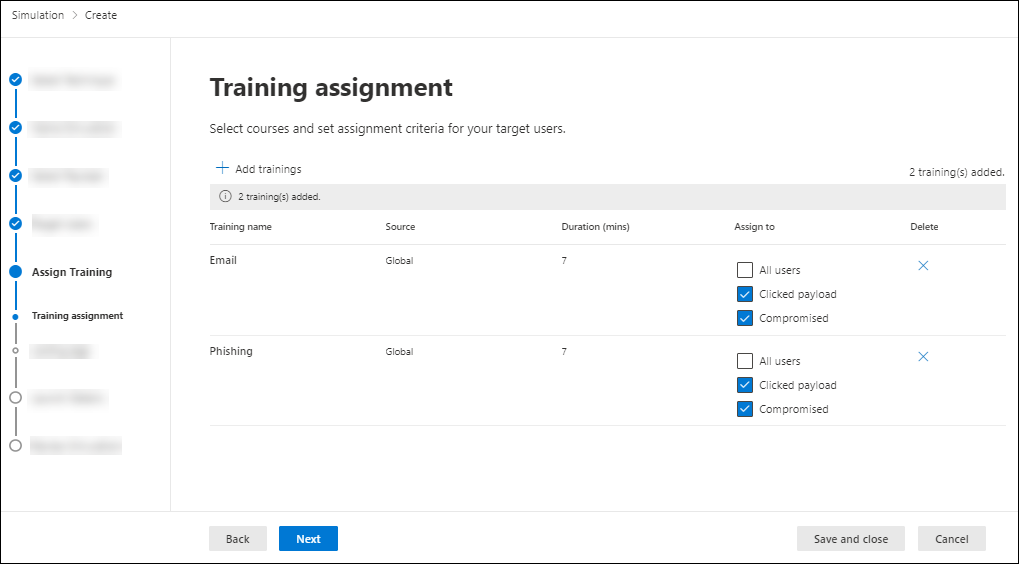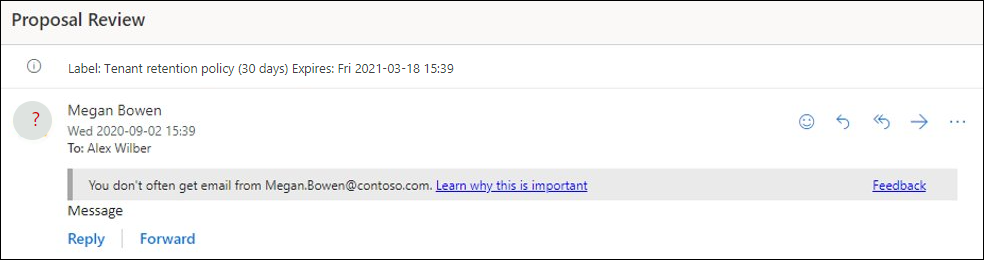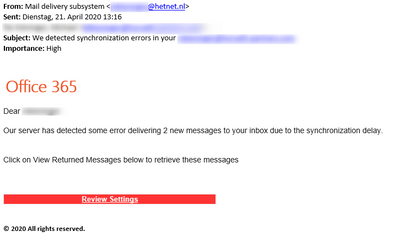
Phishing Filter - M365 ATP - false positives blocked or clear spam messages get into inbox. - Microsoft Tech Community

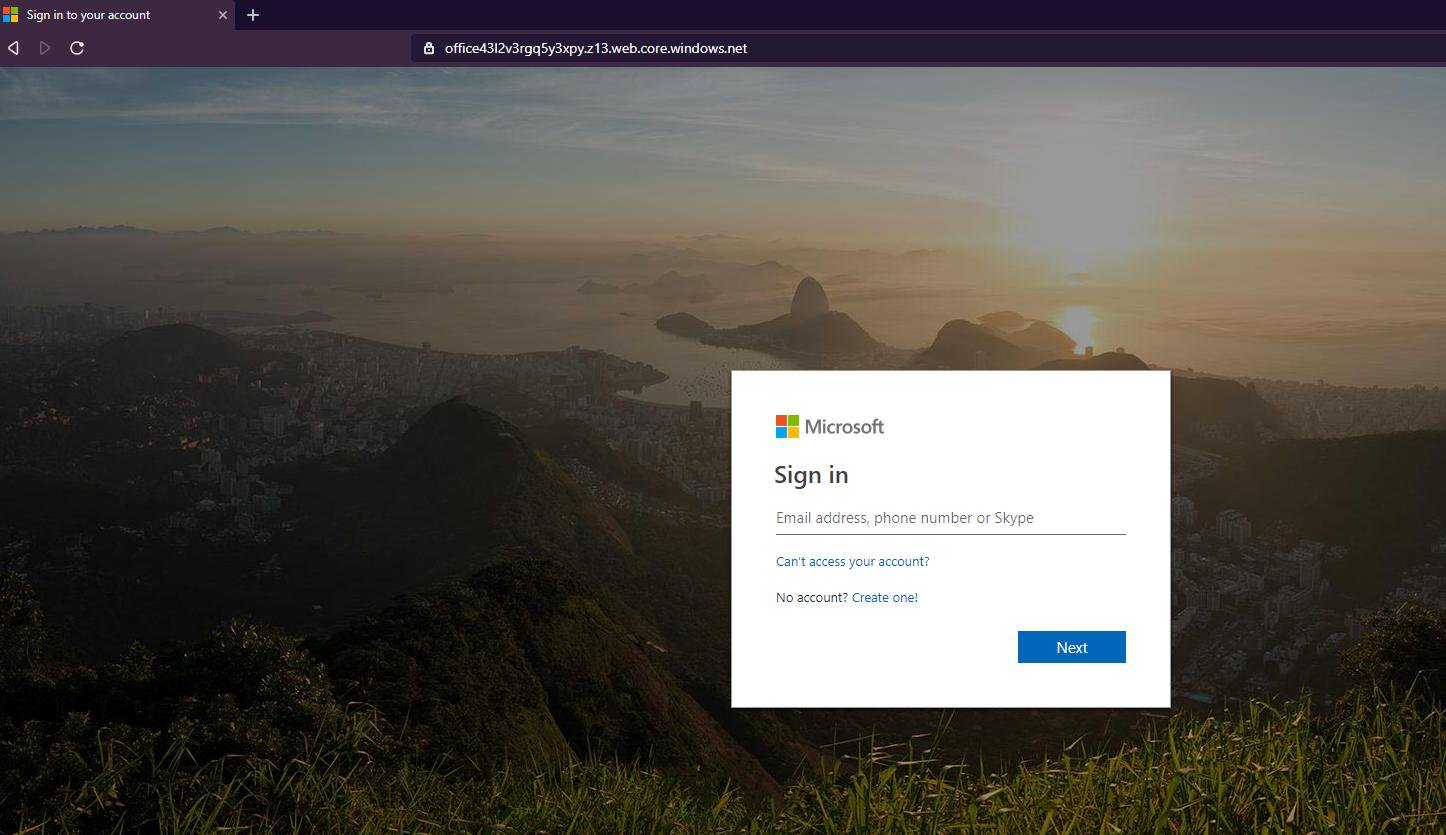
Five techniques to bypass Office 365 protections used in real phishing campaigns - Infosec Resources
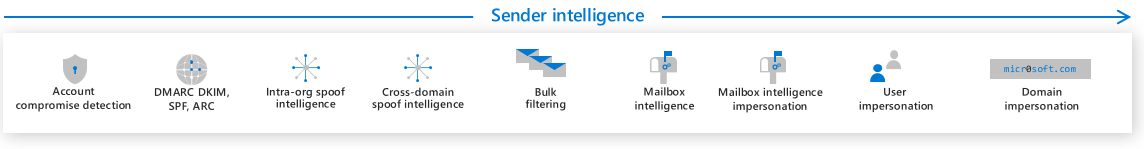
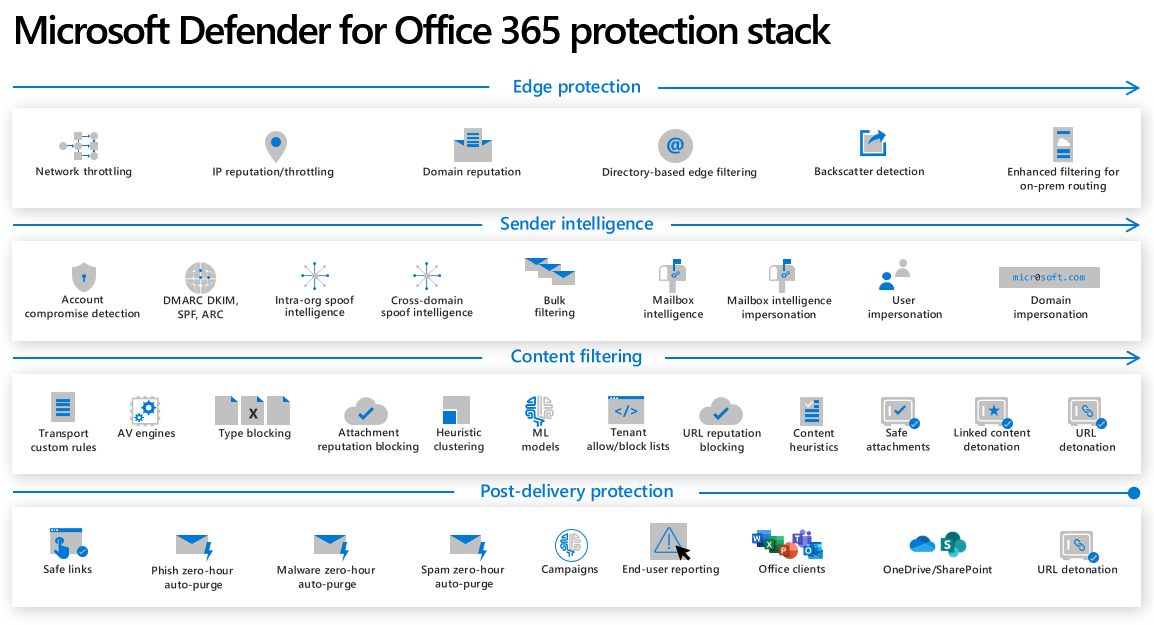
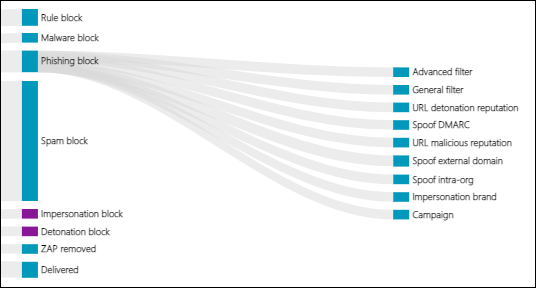
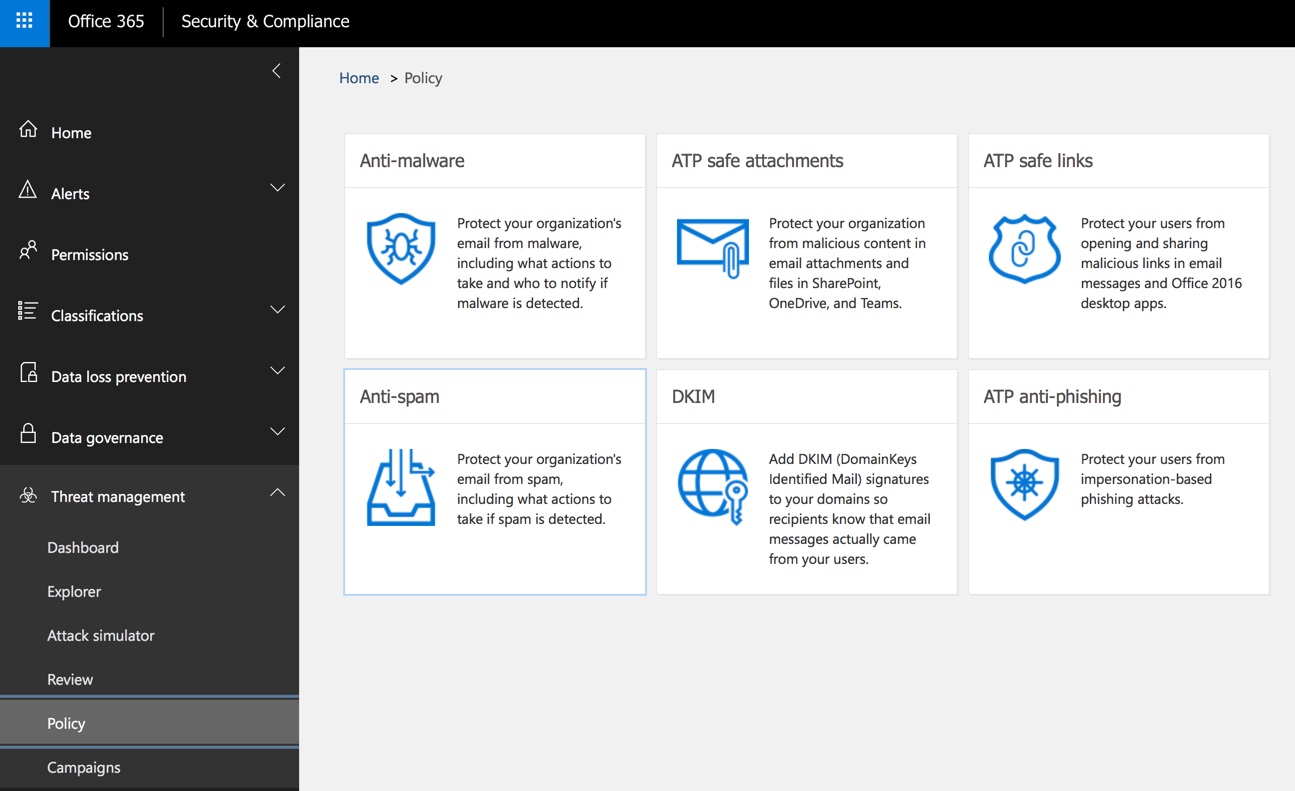
Step-by-step threat protection stack in Microsoft Defender for Office 365 - Office 365 | Microsoft Docs