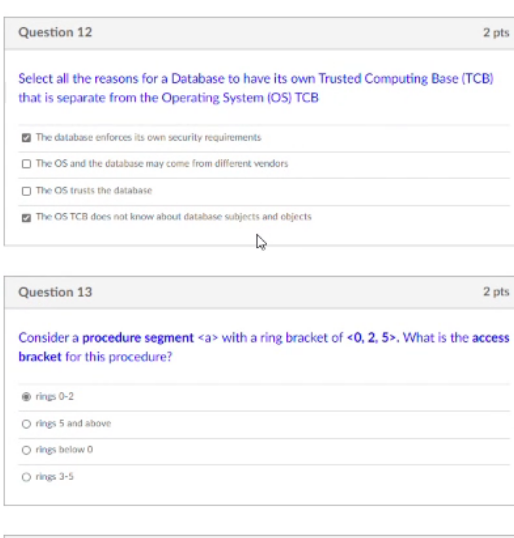
CISSP PRACTICE QUESTIONS – 20210125 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

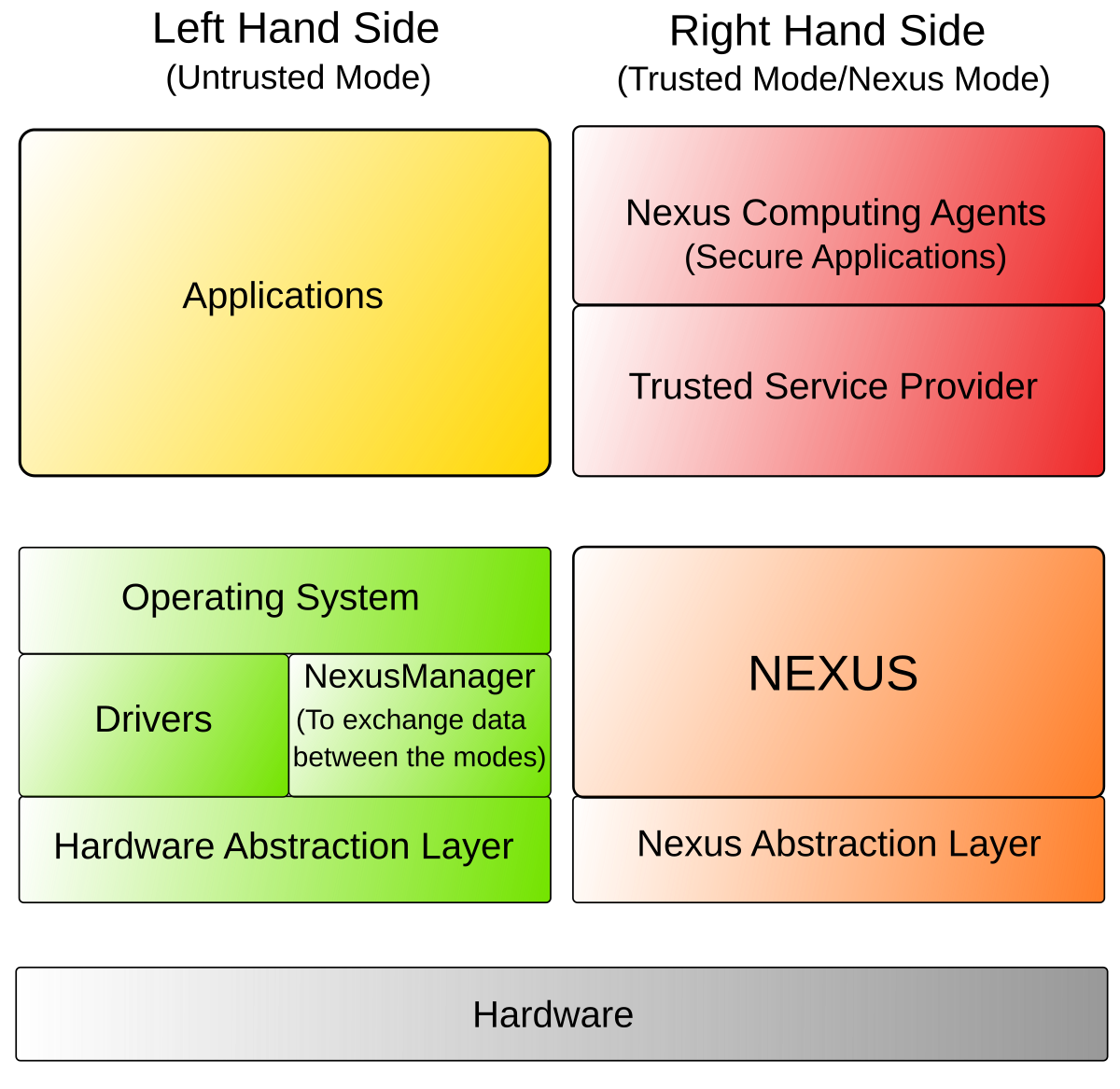
Trusted Path and Trusted Channel by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
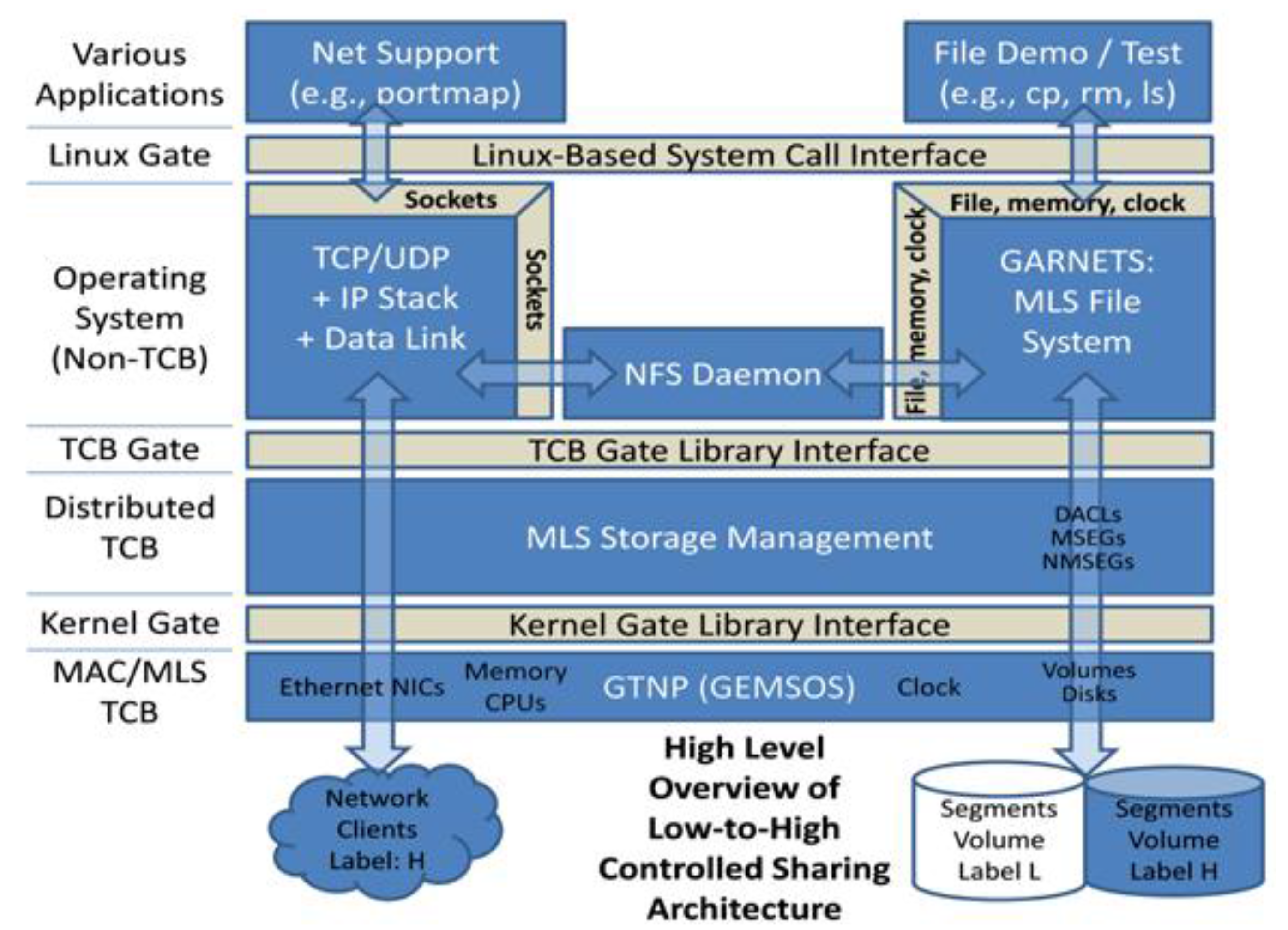
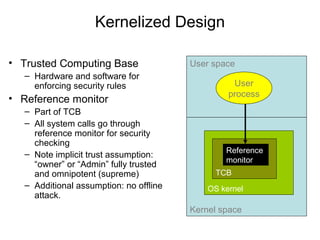
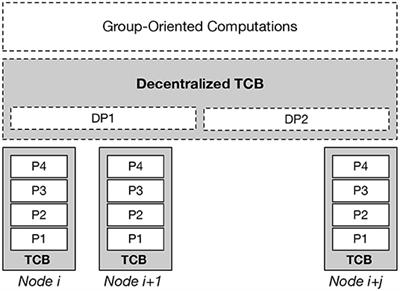
Information | Free Full-Text | Using Proven Reference Monitor Patterns for Security Evaluation | HTML
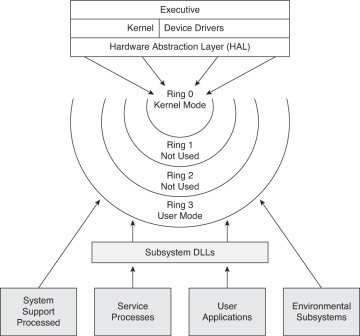
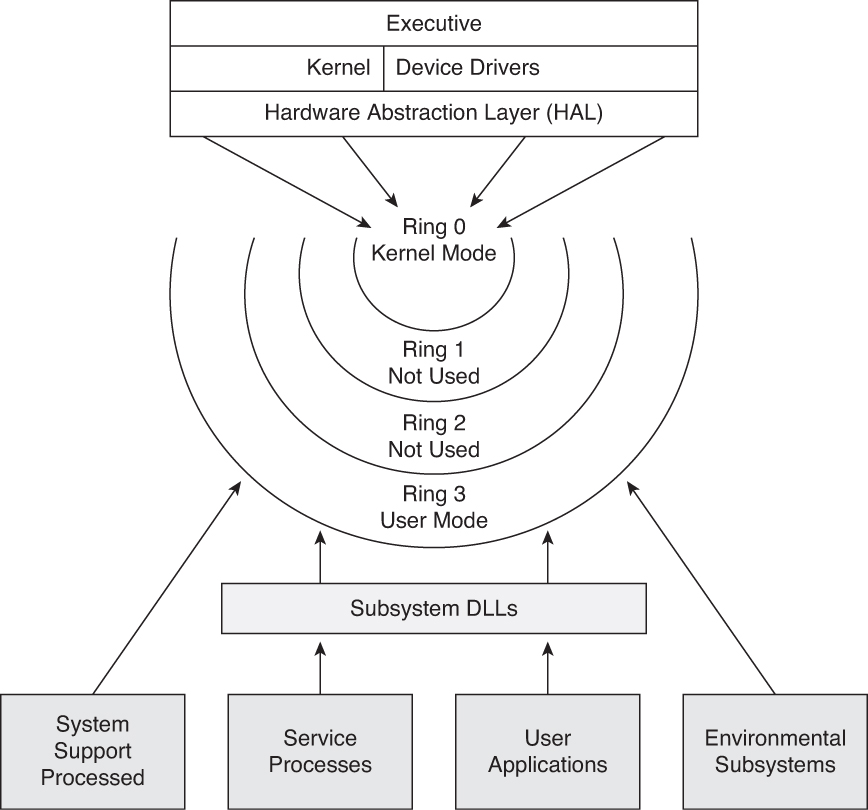
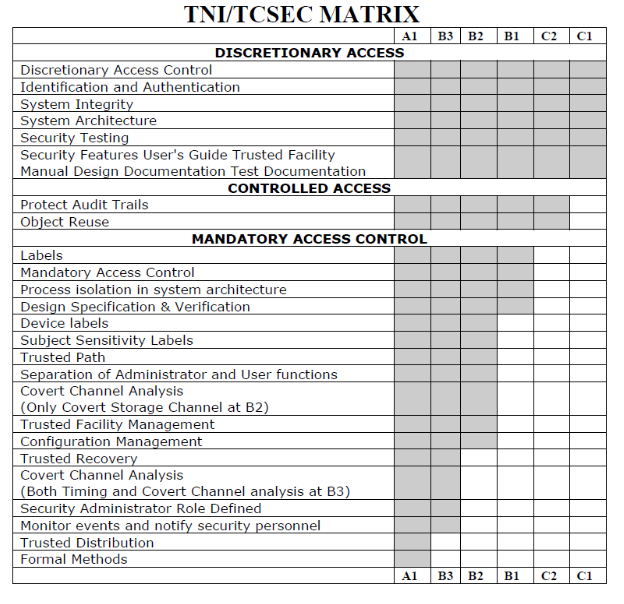
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification
CISSP PRACTICE QUESTIONS – 20190822 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu

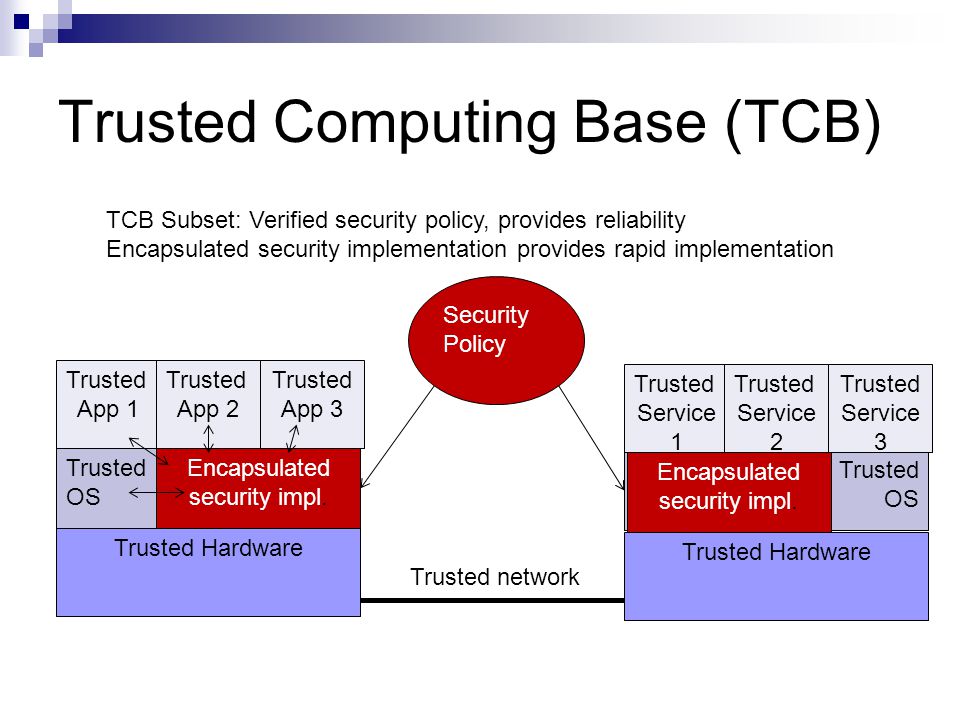
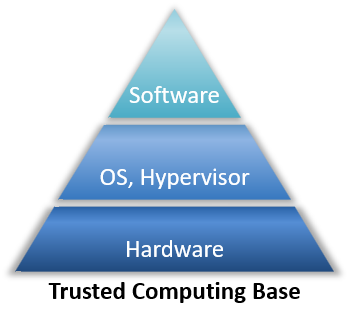
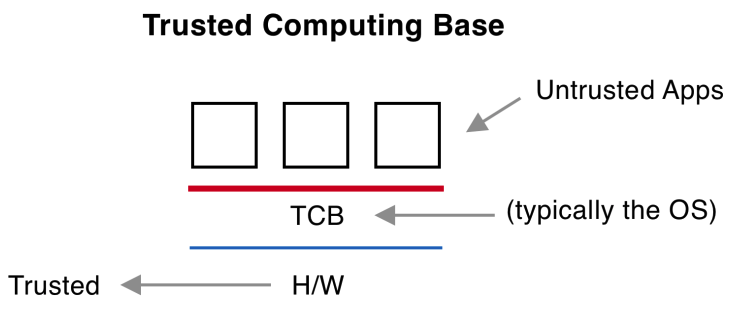
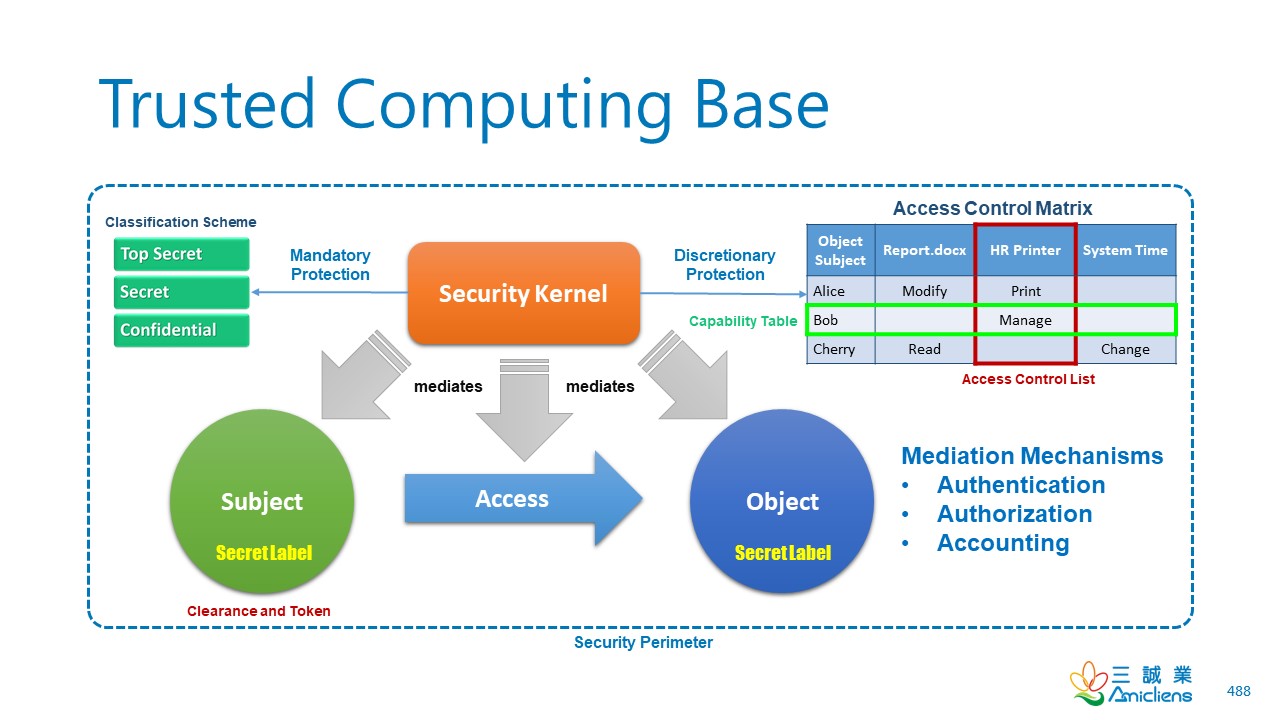
1 Security Architecture and Designs Security Architecture Description and benefits Definition of Trusted Computing Base (TCB) System level and Enterprise. - ppt download